
- Key Terms
- Introduction to the Playbook
- Critical Questions:
- What is a Political Party Digital Strategy?
- Core Function I:Internal Communications
- Core Function II: Contact Management
- What is Data?
- Updating Your Data
- Organizing Your Data
- Where to Manage Organizational Data: Databases
- What Do Databases Allow Your Political Party to Do?
- Principles for Creating a Strong Database Environment
- Data Access Policy
- How to Digitize Your Data
- How to Organize Your Data
- Advanced Data Solutions
- Transferring Your Online Data
- Core Function III: External Communications
- What Is the Ladder of Engagement?
- Key Components for Effective Digital Communications
- Crisis Communications
- How and Why Your Party Should Combat Disinformation and Hate Speech
- How to Develop a Social Media Strategy
- Digital Communication Tools
- Social Media Tools
- Digital Advertisements
- Tracking Engagement of Members and Supporters
- Campaigning
- Core Function IV: Fundraising
- Annexes
Acknowledgements
The development of this playbook was made possible through the writing and research of Diana Kurth, Maura McCrary and Amanda Zink, with extensive support by Tyler Brown at Hadron Strategies. Thanks to Bret Barrowman, Katie Harbath, Matt Lakin, and Hui Hui Ooi for their review, editing support and strategic guidance throughout the development and finalization of the playbook. Finally, thanks to the myriad of IRI staff who provided input and thorough review throughout the development process.
About the International Republican Institute (IRI)
IRI is one of the world’s leading international democracy development organizations. The nonpartisan, nongovernmental institute has supported civil society organizations, journalists, democratic governments and other democratic actors in more than 100 countries since 1983—in Africa, Asia, Eurasia, Europe, Latin America and the Caribbean, the Middle East and North Africa—with a presence in over 80 and working in over 100. The Technology and Democracy team at IRI works in every region of the world to help grassroots actors turn digitization and the technological revolution into a force for democratic progress.
Key Terms
Below is a list of key terms we will reference throughout the playbook, with their definitions.
Acquisition campaign: A campaign designed with the specific purpose of obtaining data, such as contact information (email addresses, phone numbers, etc.).
Application Programming Interface (APIs): A tool that allows data to smoothly pass back and forth between web applications, such as between your party website and your primary database.
Crowdsourcing: The practice of gathering input or feedback from a large group of people, often an external audience.
Customer relationship management (CRM): Software that centralizes your data so it is better organized, more searchable and actionable, and better able to integrate with voter contact tools, such as email, texting and advertising.
Cybersecurity: The practice of protecting networks, devices and data from unauthorized access or criminal use, and ensuring confidentiality, integrity, and availability of information.
Database: A centralized location where information from multiple lists can be housed and organized, spanning from simple spreadsheets to more elaborate CRMs.
Digital strategy: A plan to intentionally integrate digital tools into party operations in order to advance party goals and augment analogue operations.
Email file: A list of emails of contacts, including supporters, potential supporters, funders, etc.
Email service provider (ESP): A company that offers email marketing or bulk email services to assist with contact outreach and management.
File Transfer Protocol (FTP): A standard protocol used to communicate and transfer files between users over the internet.
Information manipulation: A set of tactics involving the collection and dissemination of information to influence or disrupt democratic decision-making, including misinformation and disinformation, propaganda, hate speech, etc.
Individual record: A record containing information on an individual voter, typically including the voter’s name and additional fields of relevant information, such as address, email, party affiliation, ZIP code, phone number, etc.
Information technology (IT): Technical skills and software/hardware that enable the use of, engagement with and capitalization on the internet.
Internet service provider (ISP): An organization that provides services for accessing, using or participating in the internet.
Key performance indicators (KPIs): An indicator, or set of indicators, that evaluates the success of a specific activity, often used to measure the success of advertisements, social media posts, etc.
Ladder of Engagement: A concept describing the levels of interest and engagement through which supporters and potential supporters move to become increasingly invested in your political party.
List: A compilation of individual records of prospective or current voters, volunteers, donors or any other group relevant to the campaign. Once you establish multiple lists, they can be aggregated in a database.
Listserv: An application that distributes email messages to an established electronic mailing list to assist with mass or group communications.
Segmentation: The process of breaking up a larger datafile into smaller subsets based on certain criteria, creating more homogenous groups within a broader datafile.
Tags: An additional field added to an individual record to create subsets of data that are easy to look up, sort and filter.
Virtual private network (VPN): A tool to circumvent censorship and surveillance by accessing the internet through another server instead of your own internet service provider, creating an encrypted and protected network connection.
Unique identifier: A piece of data or a code that distinguishes each individual record from other records in the list, especially useful if individual records have overlapping data points (e.g., the same address, ZIP code, etc.).
Urchin Tracking Module (UTM) tags: Extended links to identify specific traffic generated by clicking on a link from a marketing email or social media, helping to track the effectiveness of online marketing campaigns.
Introduction to the Playbook
Who We Are, Who This Is For, And Why Digitization Matters
Across the globe, there is an ongoing trend of digitization sweeping public spaces and transforming political processes, institutions and citizen expectations. This trend has been further amplified by the COVID-19 pandemic. While many established political parties have capitalized on this wave of digitization to advance their outreach and party goals, IRI has seen many others falling behind and sometimes struggling to compete with political newcomers that employ digital tools more effectively than established political parties.
This playbook is designed to help political parties of all capacity levels take steps to expand their operations online and increase their overall capacity to operate digitally.
This playbook is written specifically for political parties seeking to expand their online operations to take advantage of the unique benefits technology can provide.
Parties very early in their digitization process, but with some limited knowledge and experience with digital tools, will find this playbook particularly useful. Digitizing operations, even in limited and incremental ways, is an important step necessary for political parties to strengthen campaigns, win elections and ultimately promote stronger democratic processes and governance. Technology allows political parties to reach new audiences in new ways, communicate with a wide variety of stakeholders and become more efficient in managing communications and member information.
This playbook includes tools and best practices that can help political parties organize internal communications, mobilize supporters and conduct effective campaigns online, to name a few examples. It is important to note that while digitization can certainly be a useful tool to improve party operations, we do not believe in or promote technology for technology’s sake. Instead, we encourage readers of this playbook to first think through their party’s goals and needs, and then strategically use technology as a tool when it can be applied to reach those goals. If applied correctly, the strategic use of digital tools can make the difference between a party’s success or failure.
How to Use this Playbook
The playbook begins with an overview of critical questions political parties should always keep in mind, as well as the critical roles and functions to consider when expanding your operations online. The following sections include guidance on digitizing the core functions of a party, including how to digitize internal party communication, contact management, external communications and fundraising. Throughout, we’ve included key tips regarding critical topics such as cybersecurity and inclusion, as well as illustrative case studies.
We recommend you engage with the playbook following the steps below:
| Step 1 | Refer to the guiding checklist in Annex A (page 60) to help you understand and map your party’s needs and priorities as you use this playbook. This guiding checklist will also help you understand the nuances of what each section will cover. |
| Step 2 | Before jumping into guidance on specific tools and operations, go to page 9 to carefully consider all critical questions to be sure you have a strong understanding of what’s required, and what’s at risk, in digitizing operations before you begin. Visit page 64 to find annexes providing more detailed guidance on each of the critical questions. |
| Step 3 | Once you’ve considered the critical questions, if you would prefer to not read the playbook in full, navigate to the chapter most relevant to your party’s needs and refer to the guiding checklist (Annex A, page 60) to identify that section’s key points, skills and tools. |
| Step 4 | After reading through the playbook, take time to meet with your fellow party members and leaders, determine party needs and priorities, and create a plan for how, and in what priority, you will implement steps to digitize party operations. Keep in mind that you do not need to implement every step immediately, or even at all, if something does not make sense for your party. |
Critical Questions:
Security, Access, Inclusion, Privacy and Legal Regulations
As you consider when and how to expand your party’s operations online, and the various tools and best practices laid out in this toolkit, keep four critical questions top of mind. These questions focus on the four key elements that should be considered before, during and after every digitization decision your party makes: security, access and inclusion, privacy, and legal regulations. Keep an eye out for tailored points for each of these topics throughout the playbook. Refer to the Annexes if you need more detailed guidance in answering any of the questions posed below.
- Digital Safety and Cybersecurity
How do you assess risks to safety and security? How can you mitigate those risks? Keep in mind that cybersecurity and digital safety have real-life, physical consequences as well. Do you have a plan in place for security at both the individual and party levels? Have you proactively integrated tools and best practices—such as two-factor authentication, VPNs, password managers, etc.—into party operations? We strongly recommend referring to Annex B for detailed guidance and tools to strengthen your party’s cybersecurity. If your cybersecurity practices are not strong, all other digital aspects of your party operations will be at risk at best, or undermined at worst. Every party with a digital operation, from the simplest digital tool to the most modern and sophisticated, is a potential target for cyberattacks, which can have devastating consequences for both general operations and campaigns. - Access and Inclusion
Who are you trying to reach? Are they online? Is their internet fast enough to participate in or access what you’re trying to do? What type of equipment are they using, such as smartphones with data plans or computers with wifi capabilities? What other technologies do they already use? If most of your intended audience does not have access to technology, many of the recommendations for digital outreach will not improve your operations, and key demographics might be excluded. See Annex C for additional guidance on access and inclusion online. - Privacy
How are you keeping data secure? Are you collecting sensitive personal data? Do you need all of the personal data you are collecting? Have you built privacy and ethics into digital data collection? - Legal Regulations
Has your party taken the time to investigate, map and understand existing legal regulations governing political parties in your country, state and/or jurisprudence? Have you identified regulations related to general political party activities, campaign finance and data use? Are legal regulations different for online and offline activities? See Annex C for a list of additional questions to help your party consider and comply with legal regulations.
Now that you’ve considered the questions that are foundational to any digitization effort, the remainder of the playbook will discuss how to expand your online operations and use digital tools to benefit your work.
To start, we will introduce the concept and importance of a political party digital strategy, including its fundamental goals and how it relates to a traditional party strategy.
What is a Political Party Digital Strategy?
Even in an era of rapid technological transformation, the basic objectives of a political party remain unchanged: build a grassroots network around common principles and turn individuals out to vote. The goal of developing a digital strategy is to take the basic principles and goals of party operations and apply them to a modern, interconnected environment by taking advantage of and intentionally integrating the scale and cost efficiency offered by digital tools. Developing a digital strategy will help you maximize party impact through digital tools in an organized way.
In the early stages of digitizing your party’s operations, amid all the technology and acronyms, it can be easy to get lost in learning the technical details and lose sight of the larger picture and overall party objective.
For that reason, it is important to understand that while digital tools help to achieve greater scale, the underlying fundamentals of party work remain the same. Every political operation, small or large, is built on three fundamental roles:
- Field Work
Engaging voters, managing a volunteer network and turning out voters to the polls. - Fundraising
Building the financial resources to fund party operations. - Communications
Providing the rationale behind the party platform and disseminating it through media platforms to potential voters.
In each case, digital strategies have provided modern solutions to achieving those goals at greater scale, and have optimized speed and cost effectiveness, but the fundamentals remain the same. Short-term metrics that digital tools can provide, such as “likes” and “shares,” can be useful, but they do not replace the fundamental objectives of a political party.
Digital strategies are critical for your party, but do not rush this process. It will take time to introduce digital tools and integrate them into party operations. You cannot rush through this in a few weeks; digitization will be a sustained effort by all party members over the course of many months.
The following toolkit is intended to provide guidance on tips and best practices for running party operations online. Ultimately, it is important to remember that the best digital strategies are those that generate offline results, namely an increase in active supporters, money to fund campaigns and, most importantly, votes on Election Day.
Core Function I:
Internal Communications
Internal communications are a critical party operation. They are required to develop and maintain strong party cohesion, to establish campaign direction, to efficiently solve problems and to manage all other party functions. Internal communications can occur in person, on paper or, increasingly, through digital tools.
In this section you will find information and guidance on the below topics:
- An overview of internal party structure, including key roles and their critical functions.
- The role of an IT team.
- Tools and resources for digital internal communication.
- Tools for digital meetings and events.
- Cloud suites and internal file sharing.
Internal Party Structure
Establishing a clear internal party structure is necessary for your party to function efficiently, and to inform clear internal communication. When used strategically, technology can play a crucial role in effective communication within the party, strengthening the party’s ability to achieve its goals. A basic aspect of party management is understanding who is external and internal to the party. Before jumping into digitizing functions such as communications with external stakeholders, campaigning and fundraising, it is important to first establish an organized internal system.
The below graphic provides a loose summary of key internal positions and workflows recommended for a fully functioning and organized political party. The chart distinguishes between roles necessary for general party functions, highlighted in green, and roles necessary to fill as a party digitizes to help manage new digital tools and processes, highlighted in blue. Party structures and workflows change depending on the needs, capacities and goals of each party; the positions listed below are illustrative.
General Internal Party Structure*
| _ |
|---|
| Necessary for party operations regardless of digitization |
| Role | Key Functions |
|---|---|
| Executive Director/Campaign Manager | Oversees development of the party’s strategic plan, guides the management and growth of the party, oversees all other organizational functions/directors, etc. |
| Communications Director | Oversees external and internal messaging, manages staff focused on communications and public relations, establishes and maintains messaging of party values, directs use of communication tools, etc. |
| Finance Director | Manages party fundraising, donor prospecting, donor management, membership and database operations to raise revenue needed for the party’s core operations. |
| Treasurer | Separate from fundraising, manages party accounting and sets up internal processes to integrate accounting software with fundraising software. |
| Political Director | Manages voter contact and outreach, member recruitment, etc. |
| Legal Team | Ensures the party is following legal guidelines and regulations for the context in which it operates. |
| Coalitions Director | Is responsible for overseeing and building coalitions with likeminded groups and allies. |
| If your party is integrating digital tools, these roles are necessary hires |
| IT/Information Officer | Is responsible for the build-out, management and integration of all party technology, hardware and software. |
| Cybersecurity Officer | Manages risks posed by malicious actors to sensitive party information and data. Is responsible for identifying weak points in security protocols and training team members in best practices to be vigilant and responsible. |
| Data Director | Responsible for managing the aggregation, management, and applied use of party data. Should develop a roadmap for ensuring that the data is responsibly housed and accessible in order to guide party strategy. Trains relevant party operatives on how to incorporate data collection and data application into strategy and execution of party activities. |
| Digital Director | Oversees the build-out and deployment of software tools to further the party’s goals of voter contact, messaging and fundraising. Trains relevant party operatives on how to employ software tools for each of these goals. |
Members and volunteers should be organized in line with, and in support of, each of the roles and functions listed above.
*It is ideal to hire a distinct individual for each role. For parties with limited resources, one individual might need to serve across multiple roles and handle multiple tasks. If funds or personnel options are limited, consider hiring an external consultant. Please note that there can also be overlap between roles; for example, the digital director may overlap with the communications director, etc. Establish clear workflows internally to avoid duplication of efforts and to create a unified party.
Once your internal structure is established and staff members clearly understand their assigned roles and responsibilities, you need to consider who is communicating with which stakeholders. The below chart provides general parameters for how your party should think about internal and external stakeholders to help inform your different types of messaging.
| Internal Stakeholders | External Stakeholders |
|---|---|
| Party staff | Press |
| Volunteers/members | Voters |
| Candidates | Donors |
| Civil society organizations (CSOs), nongovernmental organizations (NGOs) and citizen interest groups |
The Role of an IT Team
When we talk about digitizing your operations, we are referring to expanding the processes and culture of your party online. Digitization is the strategy and integration of digital tools, resources and best practices to achieve your party’s offline goals, including integrating digital tools to achieve those aims. In contrast, information technology refers to the technical skills and software/hardware that enable the use of, engagement with and capitalization on the internet.
If your party has the capacity, it is beneficial to include an IT team or administrator in your management structure. Most importantly, the IT team or administrator writes your party’s incident policy or procedures when an intrusion, either external or internal, happens, so that your party is prepared when responding to a cybersecurity incident. An IT team has a few additional key roles and responsibilities:
First, the IT team or administrator serves as a technology expert within your party. They can assist staff with questions or with operating any of the tools mentioned below.
Second, they manage network functions, data security and party accounts. If a full team is not in your budget or capacity, consider an IT administrator.
Third, the IT administrator (or admin) controls who has access to which systems and files. As mentioned on page 28, this is vital to the security and efficiency of your party’s operations, as well as for respecting data governance and privacy.
The IT admin can serve in the administrator role in addition to their other duties within the party, although they should have legitimate technical experience and knowledge. Even if bandwidth is limited, having an IT admin is still very much encouraged; this can often prove more efficient than dealing with security or technical problems after they occur.
When hiring for an IT position, find an individual who already has extensive knowledge and skills managing and securing technology. They should be able to explain technical concepts to those without a technical background. Their job is to make technology seem simple and efficient for everyone else, in addition to managing cybersecurity. Another option is to outsource this role to a contractor. Keep in mind that, like all new hires, you must conduct due diligence around who you are hiring and what information they can access.
Depending on your operating environment, party members and staff should consider using a VPN if facing surveillance or censorship. Please see Annex A for guidance on cybersecurity best practices, including VPNs.
Securely Wiping a Decommissioned Computer
One important cybersecurity concept not yet mentioned is how to take care of a device no longer being used by your party and is a key role your IT administrator should manage. Over time, you will replace laptops and other devices. Similarly, your party may take advantage of donated devices. Whether onboarding or disposing of a device, it is always best to ensure that its data is securely wiped before it leaves your control, and is a task your IT team or administrator should manage. Refer to this resource for more information on securely wiping computers.[1]
[1] Klosowski, Thorin. “How to Securely Wipe Your Computer, Phone, or Tablet.” The New York Times, 31 Jan. 2022, nytimes.com/wirecutter/guides/how-to-securely-wipe-your-computer-devices.
In the remainder of this section, we will elaborate on what platforms are appropriate for managing internal party communications. However, it is important to note that not everyone needs or should have unlimited access to every platform or piece of communication. Your party should decide who needs access to which platforms and which communication channels, either to send or receive communications. We recommend sharing information only with those who truly need it.
This approach has two benefits. First, it protects the security of the information by ensuring it is not shared with more individuals than is necessary. Second, it keeps communication efficient and staff more organized when its only receiving relevant information.
Tools and Resources for Digitizing Internal Communications
Below we lay out various tools and resources that are useful for communicating with your party’s internal stakeholders.
Email messages are used to share longer and more detailed information, both externally and internally, and can be a critical tool for managing internal communication between staff members. Your party can use email for both one-on-one communication and group communication. A few secure and free options are Google’s Gmail, Microsoft’s Outlook, Yahoo!, Protonmail and Mozilla Thunderbird. [2] Virtru and Pretty Good Privacy (OpenPGP) are more encrypted email options and should be used in operating environments facing threats of surveillance.[3]
Keep in mind that party business should never be sent over personal accounts. Ensure that all communication goes through official party channels, such as staff email accounts. You can create unique staff email accounts for each of your staff members under the same platform. To simplify and stay organized, use a combination of a staff member’s first initial and last name. For example, use firstinitiallastname@gmail.com. Use this same combination for all staff members. If you work in a restricted space and have security concerns around using staff names or official emails, consider a combination of numbers or something similar that will not personally identify staff members.
Your party should keep copies of important emails for a period of time, until you know with certainty you will no longer need to access them should any questions or compliance issues arise. Your IT admin or other staff member should create an email retention policy for all staff to follow, to ensure emails are not deleted when they are still necessary. For more information on establishing an email retention policy, and how to automate it, refer to this resource.[4] You should also refer to compliance regulations set by your local or national government. If you do not want to keep emails in your inbox, you can create specific folders. For example, you can have a folder for all campaign-finance-related emails, a separate folder with volunteer questions, etc. Additionally, make sure that all your emails are backed up. For more information on backing up emails, refer to this resource.[5] Using a listserv, which is an electronic mailing list, will enable your party to send emails to a specific group or list of people within the organization without having to type out every contact individually. You can create a listserv using any available email platform.
[2] Create a Gmail Account. Accessed 17 Aug. 2022, support.google.com/mail/answer/56256?hl=en; Outlook. Accessed 17 Aug. 2022, outlook.live.com/owa; Yahoo! Mail. Accessed 17 Aug. 2022, mail.yahoo.com; Proton. Accessed 17 Aug. 2022, proton.me; Thunderbird. Accessed 17 Aug. 2022, thunderbird.net/en-US.
[3] Virtru. Accessed 17 Aug. 2022, virtru.com; OpenPGP. Accessed 17 Aug. 2022, openpgp.org.
[4] “Assign and View Retention Policies on Email Messages.” Microsoft. Accessed 17 Aug. 2022, support.microsoft.com/en-us/office/assign-and-view-retention-policies-on-email-messages-3e5fd2dc-633f-4a38-b313-b31b81f7cf7a.
[5] Nield, David. “How to Back Up Your Most Important Emails.” Wired, 24 Jan. 2021, wired.com/story/how-to-back-up-email/.
How to Create a Listserv

| 1 |
|---|
| First, decided who you would like the listserv to target. For example, a listserv can include staff from a specific branch office or all staff working on finance. |
| 2 |
|---|
| Then, create the group and add all the members’ email addresses. Name the listserv in a way that makes clear who the members are. For example, if your listserv is for staff working on campaign finance, name the listserv Campaign Finance Staff. |

| 3 |
|---|
| Once this system is established, you can write an email, click the listserv to which you want to send it, and then send the email. When you send the email, it will go to the inbox of everyone on the list. |
Messaging Platforms
Messaging is useful for quick and casual communication between party staff. Messaging is most appropriate for quick questions or updates. Because communications through messaging platforms are more difficult to track, anything you want staff to be able to reference later should be sent as an email.
- Slack is a messaging platform that allows you to create channels on different topics such as specific candidate campaigns, finances or teams. Individual staff can join specific channels relevant to their work. Slack also allows you to message a single colleague or conduct direct video and voice calls. There is a free version of Slack, as well as paid versions that give you access to additional features.
- Google Chat has features similar to those of Slack, but will automatically integrate with your Google account. This is particularly beneficial if your party is already using Google Drive or other pieces of Google’s GSuite. GSuite tool integration enables you to share Google Doc files in the chat or add your chat to your Gmail inbox and use Google Chat directly in your email. Google Chat has one-to-one messaging capabilities. It also has spaces, similar to Slack channels, that allow you to message multiple people in a group. You can set up a different space for each of your needs and invite relevant staff to join each space. Additionally, Google Chat has a “meet feature” that allows you to set up and join meetings through video or audio. Google Chat, previously called Google Hangouts, is a free service.
- Microsoft Teams Chat has features similar to those of Slack and Google Chat, and is especially efficient if your party is using Microsoft’s Microsoft365 platform, as it easily integrates messaging into your day-to-day operations. Microsoft Teams allows you to have one-to-one messaging chats, specific team chats, and video and audio calls. If you use Microsoft365, Teams will also integrate into your Outlook Calendar and allow you to view recently accessed files. Microsoft Teams has a variety of plan options, ranging from free to $12.50 per month.
- Signal is a messaging app with end-to-end encryption, meaning no one, not even Signal, can see or hear your messages or calls. Signal has options for group chats as well as video and audio calls. Signal is free and is a great option to ensure secure messaging.
- WhatsApp, operated by Meta (formerly known as Facebook) is another messaging application with end-to-end encryption for its users. WhatsApp allows you to create group messages, as well as to conduct video and audio calls. WhatsApp is free.
- Facebook Messenger, also operated by Meta, is linked with your Facebook account. This app allows you to message individuals or groups, as well as conduct video and audio calls. Facebook Messenger is free.
- Telegram is a messaging application that has options for group chats, as well as video and audio calls. It does not automatically enable end-to-end encryption; if you want the security of end-to-end encryption, you must enable it through the “secret chat” function before sending messages through the app. Secret chats don’t sync between devices, so Telegram is better for conversations that are not sensitive. Telegram is free.
- SMS Texting can be useful when your staff does not have the bandwidth to support the above applications. It can also be used for one-on-one communications or group communications.
Project-Management Tools
A project-management tool can be useful as the number of digital tools you are managing grows. Tools such as Asana or Trello can help ensure internal leaders, staff and volunteers have the resources and awareness they need to achieve communication goals and maintain accountability on their assigned responsibilities.[6] These tools can be costly, so only consider integrating these tools once you research their costs and are able to identify funds for their use.
[6] Asana. Accessed 17 Aug. 2022, asana.com/campaign/fac/do; Trello. Accessed 17 Aug. 2022, trello.com/en-US.
Tools for Digital Meetings and Events
In addition to day-to-day communication, technology provides efficient ways to bring together individuals for conversation. Meetings and events can be hosted virtually on a video-conferencing platform, or in a hybrid manner, in which some people join virtually and others attend in person. Video conferencing provides benefits for a variety of needs: traditional meetings involving multiple speakers and active participant collaboration; presentations and trainings, in which one person does most of the speaking; and panel discussions with multiple speakers and an audience.
Common video conferencing platforms include:
All of the above platforms have both free and paid versions. Using a digital tool to create a virtual option for a meeting or event allows participants to join from where they are, reducing the need for everyone to travel to a meeting location or come into the office. This creates extended options for participants and greater flexibility. When conducting training for staff, consider a hybrid option in which staff members participate in person but a trainer joins virtually; this allows more options for possible trainers. Additionally, virtual meetings can connect multiple branch offices to one central meeting.
A virtual meeting allows you to incorporate many unique features, such as chat boxes, polls, Q&A boxes, breakout rooms, whiteboards, screen sharing, recordings and replays. All the products mentioned above have frequently asked questions (FAQ) pages with more information on how to operate each of these tools.
Key Tip: Accessibility
Keep in mind that video conferencing platforms use a lot of bandwidth. For low-access environments, try turning off your video when your connection is unstable, turning off incoming video of other participants, or sticking to audio calls instead of using video. Apps like WhatsApp are also good to consider in low-bandwidth areas.
Simple conference calls: When you are operating in an area with low bandwidth, use audio only. Platforms like Dialpad or RingCentral make simple, cheap, conference calls possible when video calls are not possible.
Below are a few tips and best practices for hosting virtual meetings:
- Take logistics seriously. Do not assume you can figure out how to use this technology as you go along during the meeting. Make sure all logistics are accounted for and tested in advance.
- Enable a host/co-hosts.
- One person should be designated the “host” of the meeting and have access to more tools than meeting participants.
- Have at least one additional person on hand, the co-host, to help troubleshoot, monitor the chat, take notes/screenshots, etc.
- Clearly define roles ahead of time. Who is facilitating the meeting? Who is tech support for participants? Who is the chat moderator?
- You can record the meeting when you want to refer back to the content. You should store this recording in a secure location—and if the meeting covers a sensitive topic, it may be best not to record it. Always get informed consent, ensuring that participants understand they are being recorded and what you are planning to do with the recording (such as post it online, save it for future reference, take better notes, etc.).
- Mute attendees when they are not speaking, and request that participants unmute when they would like to talk. You can also turn off someone’s video if they do not have enough bandwidth or are distracting other participants.
- Screen sharing can help your participants engage in the meeting by giving them a visual to follow. You can share a specific presentation, a website or a file.
- Conduct tutorials in advance with those unfamiliar with the technology.
- Test all audio and visual elements (microphone, screen sharing, etc.) before the webinar.
- Take advantage of all the tools these platforms have to offer and build regular interaction into the format—Q&A, polls, breakout rooms—to keep participants engaged.
- Encourage the use of the chat function so participants feel engaged, shyer individuals can more comfortably participate and the flow of the presentation isn’t disrupted by random comments or side conversations.
- You can configure many of the above settings to be default or change them around for each meeting, depending on the audience and your needs.
For hybrid meetings, don’t forget to include those on camera in the discussion. Ask them to raise their hand so you know they would like to speak, encourage the use of the chat function by all participants, and ensure those on camera can hear everyone in the room.
Quick Checklist for Meeting Security:
- Establish a waiting room: This enables your team to monitor who joins the meeting, and only allow accounts you recognize to join. It also allows presenters and moderators to join early and set up before all meeting participants are allowed to join.
- Establish a meeting password: This limits participants only to those who have received the password.
- Require authentication: For sensitive meetings, require users to sign into their correct account to authenticate their identities before they can request to join.
- Enable encryption: For sensitive meetings, enable encryption for your meeting to protect against interception of the discussion and data shared.
For more information on operating engaging meetings and webinars, making the technology work and running effective meetings, please refer to this resource.[7]
[7] Zenhom, Omar. “5 Proven Strategies for Engaging Webinars.” Medium, 1 Dec. 2017, medium.com/@omar_31102/5-proven-strategies-for-engaging-webinars-6ceaf01ce440.
Cloud Suites
For a party to operate online efficiently and securely, members, staff and volunteers will need access to central file storage and collaboration tools. Cloud-based services are an important piece of internal management, and are a secure way to store your files and communicate. Cloud-based services store your information on servers managed by third-party companies, such as Google, Microsoft, or Dropbox. The benefit of storing your files on the cloud instead of on your computer is that you receive a higher level of security, multiple individuals can collaborate on a document at once and your files are better protected if your physical device is broken or compromised.
There are a variety of general cloud-based office-suite platforms that provide a variety of services for your party. For example, Google’s Google Workspace offers Google Drive for file sharing, Gmail for email, Google Hangouts for chat, Jamboard for collaboration during meetings and Google Docs for specific files. Microsoft’s Microsoft365 is another option that provides OneDrive and SharePoint for file sharing, Outlook for email, Microsoft Teams for chat and calls and Microsoft Office for specific files.
Protect Your Democracy is a service offered by Google to provide extra protection against phishing for Gmail as well as protection for websites against cyberattacks. AccountGuard is a similar service offered by Microsoft to help political organizations protect themselves from cybersecurity threats.
Your party can tailor these cloud-based office suites to its needs, but basic training on how to operate and organize them will be necessary to ensure the whole party understands how to use them. Additionally, you will need to update your system whenever a new update is required. Refer to the security annex for information on how to check for updates and how to update your systems.
Other Applications for Digital Internal File Sharing:
- DocuSign allows your party to share documents for signature.
- Adobe PDF allows your party to create, read and edit PDF files.
- Dropbox gives you the ability to store and share files.
Core Function II: Contact Management
The most valuable resource for any political campaign is people. In order to meet its goals, the party must recruit candidates, hire staff, develop volunteers and turn out citizens to vote at the polls. Managing contacts and voters and growing a party’s membership and support base requires a lot of information, which can also be referred to as “data.” A party needs to know the answer to many questions. Who are these people? How do you contact them? Where do they live? Do they donate? Do they volunteer? Do they vote? This information helps the party design its electoral strategy and get the most out of its existing resources. Contact management is the process of collecting and managing that data to successfully maintain relationships with your supporters and potential supporters, and ultimately build an infrastructure of support for your party.
This section includes guidance on the following topics:
- What data is and how to structure it.
- How to segment party data.
- Where and how to manage organizational data.
- An overview of databases: what they are, why they’re helpful and how to manage them.
- Available tools, such as customer relationship management software, to help manage data.
What is Data?
Data is the lifeblood of a strong political party operation. A good data operation begins with the mindset that you are always looking to collect new data. In every engagement (whether you are looking for new donors, to win over voters, etc.), everyone has the responsibility to collect data that they bring back to the data director so the party as a whole can benefit from the data collection. Staff will come and go, taking with them institutional knowledge, but the party’s database creates a living memory for future reference and more informed decision-making.
Data collection, housing and management are team responsibilities and should be emphasized at every level of party operations. Invest in training all staff on the importance of data and how to build it into daily operations. Make the process of uploading new data accessible so that all staff can easily add new data to the system.
The topic of data can be confusing for novices and seasoned campaign veterans alike. Therefore, it is important to begin with understanding the basic building blocks. At its most basic, data consists of a large group of individual records.
In the context of party operations, each individual record consists of a name and additional useful fields, such as an address, phone number, email or other relevant information.
Example 1, Individual Record
| Last Name | First Name | Address 1 | City | State | Zip Code | Country | Phone Number |
|---|---|---|---|---|---|---|---|
| Smith | John | 123 Main Street | Washington | DC | 20005 | US | 999-999-9999 |
When multiple individual records are combined, they become a list. A list could be a compilation of individual records of prospective voters, volunteers, donors or any other group relevant to the campaign.
Example 2, List
| Last Name | First Name | Address 1 | City | State | Zip Code | Country | Phone Number |
|---|---|---|---|---|---|---|---|
| Smith | John | 123 Main Street | Washington | DC | 20005 | US | 999-999-9999 |
| Álvarez | Maria | Carrera 1 No. 10 | Bogota | Null | 110211 | Colombia | +5713171313 |
| Rasid | Mawar | 79 Cedar Ln | Kuala Lumpur | Null | 50450 | Malaysia | +60327191333 |
Data Collection
Data can be collected from multiple sources, including, but not limited to:
- In-person events.
- Identifying potential supporters through volunteer door-knocking or phone banking.
- Online web forms.
- Publicly available data sources.
- Commercial sources, such as mobile-phone registries and consumer data.
- Politically aligned third-party organizations.
As the list grows, it will become important to have a simple method for itemizing and distinguishing individual records. It is common for different individuals to have the same name, or for multiple family members to share details such as an address and phone number. For that reason, every individual record should contain a “unique identifier” that distinguishes the record from other records in the list. Some lists use email addresses as such a unique identifier. The ideal solution is to append a unique numeric code to each individual record to help distinguish it, even in cases in which two individuals share an email address.
Example 3, Unique Identifiers
| Unique ID | Last Name | First Name | Address 1 | City | State | Zip Code | Country | Phone Number |
|---|---|---|---|---|---|---|---|---|
| 729358 | Smith | John | 123 Main Street | Washington | DC | 20005 | US | 999-999-9999 |
| 139724 | Álvarez | Maria | Carrera 1 No. 10 | Bogota | Null | 110211 | Colombia | +5713171313 |
| 989834 | Rasid | Mawar | 79 Cedar Ln | Kuala Lumpur | Null | 50450 | Malaysia | +60327191333 |
As a campaign becomes engaged in collecting data on multiple fronts—such as through voter contact, fundraising, recruitment, etc.—it will quickly begin to develop many lists. These lists could exist on multiple spreadsheets, across multiple computers and amongst multiple staff members. This can quickly become disorganized, which is why a database is useful.
In this sense, a database is a centralized location where information from multiple lists can be housed and organized, spanning from simple spreadsheets to more elaborate customer relationship management (CRMs) software.
A database should contain security measures to ensure it is protected and is accessible only by authorized members of the campaign. Although the individual records in the database may come from multiple sources, the unique identifiers help to maintain the integrity of the data.
Tags
Tags can be a simple and effective way to organize and maintain your database. A tag is an additional field added to individual records to create subsets that are easy to look up and sort. These subsets could include the data source, issue preference or any other simple identifier to lump groups within the larger database. For example, you could use tags to mark each individual who cares about environmental policy or who signed up at a specific campaign event.
| Unique ID | Last Name | First Name | Address 1 | City | Country | Phone Number | Tag #1 Source | Tag #2 Children |
|---|---|---|---|---|---|---|---|---|
| 729358 | Smith | John | 123 Main Street | Washington | US | 999-999-9999 | Web Sign-up | 0 |
| 139724 | Álvarez | Maria | Carrera 1 No. 10 | Bogota | Colombia | +5713171313 | Web Sign-up | 3 |
| 989834 | Rasid | Mawar | 79 Cedar Ln | Kuala Lumpur | Malaysia | +60327191333 | Event #1 | 1 |
A robust, extensive data operation comes from assembling, aggregating, appending and standardizing information from multiple sources in order to have a broad perspective of understanding and engage important audiences.
When gathering data from multiple sources, you want to create consistency in how the data is organized. For example, some sources may list “full name” as a field, while others break this information into multiple fields, such as “first name” and “last name”. Similarly, some sources may break “address” information into its component parts, such as “street number”, “street name”, “city”, etc.
When building your database, you will need to decide how to structure this information. There is not a right way or wrong way to do this. That said, it is typically easier and recommended to work with data that has been broken down into its simplest component parts. This will make it easier to sort or segment the data in the future. A great reference for structuring data can be found in Hadley Wicham’s “Tidy Data.”[8]
Make sure to use consistent naming conventions. As your party grows, so will the number of people responsible for collecting the data. Those individuals may use similar but different words to convey the same concept. For example, voters may identify the following list of ideas when expressing their most important issue: “clean air,” “pollution,” “smog,” etc. A better solution would be to identify a consistent category name that can be used repeatedly throughout the dataset—in this case, perhaps “environment”—and use this to sort related concepts into the same group. Enforcing consistency in the terms used to tag individuals will make it easier to sort and segment data.
[8] Wickham, Hadley. “Tidy Data.” Journal of Statistical Software, vol. VV, no. II, 2014, vita.had.co.nz/papers/tidy-data.pdf.
Just Say “No” to “Notes”
It is a common instinct to add notes at the end of a row for new data that doesn’t fit easily into existing fields, as in the next example. Build the self-discipline to create a category for each new data point to be used consistently across the party, so it can be queried in the future.
Example 1
DON’T
| Last Name | First Name | Address 1 | City | Notes |
|---|---|---|---|---|
| Smith | John | 123 Main Street | Washington, DC | Passionate about veterans’ issues and available to volunteer on Saturdays. |
The problem with creating generalized, catch-all data fields is that they can make the information difficult to find as the database grows. Notes can become laborious to sort through and read. A better solution is to create new fields or classification categories—such as “issue preference”—in cases where you have decided the information is important and deserves to be included in the database.
Example 2, Including New Fields for Issue Preference and Volunteer Availability
DO
| Last Name | First Name | Address 1 | City | Issue Preference | Volunteer Availability |
|---|---|---|---|---|---|
| Smith | John | 123 Main Street | Washington, DC | Veteran’s Issues | Saturdays |
As a party grows, so does the need to organize and manage its data. That data could include the organization’s staff, volunteers, supporters, advocates, donors and prospective donors, in addition to all their actions. These records help the campaign better manage its resources and help identify effective strategies to pursue.
Integrating Data Throughout Party Operations
Now that you understand the core components of data and the basics of managing them, look for icons throughout the rest of the playbook to indicate opportunities to either collect data from supporters or potential supporters or apply existing party data to increase the efficiency and efficacy of your operations. As we mentioned above, data is the lifeblood of your party—it helps you identify, communicate with and manage supporters and potential supporters; informs your party of voter interests and priorities; and helps you to effectively communicate with key audiences, among other key tasks. In order for data to truly transform your party’s capacity, you need to collect and use it at every opportunity.
- Data-collection opportunity: Wherever you see this icon throughout the remainder of the playbook, it indicates an opportunity for your party to collect data, either digitally or analog.
- Data-application opportunity: Wherever you see this icon, it indicates an opportunity for your party to use existing party data to strengthen your operations, such as using data to guide targeted outreach, communicate and fundraise more effectively, etc.
Updating Your Data
It is important to recognize that the records in your database are never static. People in your audience will often move to new addresses, change their phone number, change their email, etc. As such, you will need a consistent process to update records accordingly. Over time, a messy database will be less effective for meeting your campaign needs.
The following strategies are useful for managing a “clean” database that is up to date and reducing the likelihood of duplicating records.
- Centralization: All data should exist in one central, master database. This ensures that when a record is updated, that update is reflected for all users accessing the data.
- Validation: Ensure that the data entered for each field is formatted appropriately. For example, all emails should contain an “@” and “.” in the places one would expect (e.g., fullname@gmail.com). Likewise, phone numbers should strictly contain numbers in line with the respective country’s conventions. Most CRM solutions are designed to include this validation as a feature, but validation can also be implemented in Excel by searching for “Validation” under the “Data” tab in the header.
- Integration: Take the time to properly integrate your CRM with your other digital tools, such as your website and email service provider (ESP). Again, many consumer and enterprise-level CRM solutions have an “Integrations” feature that will allow you to easily connect your data to other frequently used digital marketing tools.
- Implementing a unique identifier: As mentioned above, the unique identifier plays an important role in connecting new data with a person who already exists in your database. For example, if John Smith (johnsmith@xxx.com) were to sign up on your website, but johnsmith@xxx.com already exists in your database, the system will know that they are one and the same. Thus, the system will update the existing record rather than creating a new record. If his phone number or any other information changed during the intervening period, the existing record would be updated with this new information.
Organizing Your Data
Once you have the individual pieces of data, you’ll need to consider how to group the information you’ve collected. Below are suggested ways to structure data around audience type, such as members, volunteers, supporters and donors, as well as the specific information you should try to collect for each audience. Note that some individuals will fall into multiple groups. This is where the unique identifier referenced earlier becomes important for clarity and protecting against redundancy.
- Members
- Organization: Who are the members of your campaign organization?
- Hierarchies: Who in your organization does this individual manage or who manages them?
- Roles and responsibilities: What tasks and deliverables are that individual’s responsibility?
- Internal performance metrics: Track and report the goals for individual team members.
- Volunteers
- Long-term relationships: Who are the volunteers willing to support your organization year after year?
- Optimal or preferred volunteer activities: What types of volunteer activities is that individual best suited to perform or most interested in supporting?
- Volunteer assignments: What goals are assigned to each volunteer?
- Internal performance metrics: Track and report each volunteer’s performance.
- Supporters
- Potential voters: Voters who could reasonably be expected to support the political party.
- Vote history: How frequently the voter participates in elections.
- Issue preference: What issues are the primary motivators for the potential voter.
- Voter contacts: When and how the potential voters were contacted by the political party, such as door knocking, phone call, emails, etc
- Donors
- Donation level: The gift amount provided by the donor.
- Giving history: How frequently the individual or group provides a donation to the party.
- Giving preferences: The types of campaigns donors give to, such as campaigns with reporting deadlines, merchandise, or recurring donation campaigns.
- Issue preferences.
Where to Manage Organizational Data: Databases
Once your organization begins to accumulate useful data, the next question is how to store and manage that data. Databases provide a singular location to house and manage that data, and to easily put it to work.
While a large range of database solutions are available, for the purposes of this toolkit, the concept of a database includes tools ranging from a very simple spreadsheet to more advanced CRM tools.
In this sense, a database is a solution that allows you to store data in a single, secure location and allows your organization to continually access, update and segment that data to meet the party’s needs.
What Do Databases Allow Your Political Party to Do?
Databases help make your party’s data more organized and powerful. They support three important use cases that help the party’s data become more dynamic and powerful.
- Querying: As a party’s data becomes larger and more diverse, it becomes important to conduct searches in order to surface data that meets specific criteria. These searches (referred to asqueries) can quickly identify specific data such as new entries from the prior month, donors above a certain threshold, volunteers in specific locations and much more.
- Segmentation: After a successful query, you might want to create subsets of the larger datafile that meet particular criteria. By creating a subset, or segment, you can perform certain tasks such as analyzing performance, exporting the segment to another tool such as the party’s ESP, creating neighborhood door-knocking lists for volunteers, performing donor calls, etc. Segmentation is a powerful strategy that allows a party to focus its energy and resources on the subgroups within an audience that are most likely to take action.
- Integration: Many powerful cloud-based web applications, including those for email, social media, web forms and other tools, make use of application programming interfaces (APIs), which allow data to pass back and forth between web applications such as the party website and the database. Not only does this allow for seamless transfer of data, but it gives less technologically savvy users the ability to manage these tools without extensive experience as a database administrator.
Security Tip:
A tactic known as “bugging lists” is the practice of entering a fake name with contact information that is known to one trusted person. When conducting outreach to the list, remove the fake contact. If this trusted person receives a communication to their address using the fake name, you know your list has been compromised and someone else is using it to send information.
Principles for Creating a Strong Database Environment
A successful database solution, regardless of whether it involves spreadsheets or a more advanced option such as CRMs, should prioritize the following four principles.
Data access: Access is about making data available to users. In this case, users refers to internal party staff, leaders and volunteers who have been specifically trained and authorized to engage with the party’s data.
Databases support good data access because:
- Large volumes of data can be stored in one place.[9]
- Multiple users can read and modify the data at the same time.
- Databases are searchable and sortable, so the data you need can be found quickly and easily.
The data structure is extendable and can be modified as requirements change.
Data integrity: Databases can ensure that the data contained within them is correct and accurate—otherwise known as data integrity. Database software often uses consistent rules to provide the managers with confidence that their data is up to date and correct. For example, it may employ consistent rules, such as those listed below, to overwrite new information for a specific record.
- Consistency: Before data can be changed in a database, it must be validated against a set of rules to ensure accuracy and removal of errors such as misspellings.
- Isolation: Databases allow multiple changes at the same time, but each change is isolated from others.
- Redundancy: In addition, databases will have mechanisms for backup, distribution and redundancy to ensure data is not lost. Remember to back up your data so that when technical difficulties arise, you can always turn back to a recently saved copy.
Data security: While administrators can control access to data files or spreadsheets through passwords and permissions preferences, once someone has access to a file, they have access to all data within that file. Databases should be made very secure, and that includes the ability to have access rights to specific parts of the database but not others.
- Databases allow access to be controlled, allowing users to have different privileges. For example, some users may be able to read data but not to write it.
- Data can also be segmented so that users can access only certain parts. For example, a user may be able to read a voter’s address but not their voting history.
- Sensitive data, including personal data on Excel sheets, can often be passed, shared, emailed, etc. Microsoft Excel has the option to protect data that might be shared by enabling a password to limit access to sensitive data only to those who have the password. To do so, find the “Review” in the header menu and select “Protect Worksheet” and enter your selected password. For more information on encrypting data, refer to this resource.[10]
[9] Keep in mind this is not always advisable when operating in semi-authoritarian systems where security systems are, or have the potential to become, weak.
[10] “Require a Password to Open or Modify a Workbook.” Microsoft. Accessed 18 Aug. 2022, support.microsoft.com/en-us/office/require-a-password-to-open-or-modify-a-workbook-10579f0e-b2d9-4c05-b9f8-4109a6bce643.
Data Access Policy
Develop a simple one-page party data access policy that clearly defines which party officials and staffers are allowed access to which segments of the database. For example, the executive director and/or data director may have full access, whereas the finance director only has access to the donor file.
This policy should address questions such as: What access do candidates and their staff have? Is access restricted to specific data they need to know? Who in the party has responsibility for managing the distribution of login credentials? Which roles should have the ability to update the database?
Finally, it is a good practice to develop a data user agreement that all users must sign before they receive credentials to access the database. This document should outline limitations for how the data should be used, confidentiality expectations and enforcement measures.
- Data responsibility and privacy: Anytime the party is working with the personal information of stakeholders—whether those accessing the data are volunteers, voters, donors, website visitors or any other constituency—it is important to do so with great care. Any breach in security has the potential to reflect poorly on the political party and ultimately undermine its credibility with the electorate. All data should be managed in a secured environment (see the short section on data security above), and any sensitive data managed with extra layers of physical and cybersecurity. Database managers should ensure that only necessary and useful information is collected and stored.
How to Digitize Your Data
The decision to move your party’s data online can often be intimidating due to the fear of spending many hours uploading data captured on paper to digital tools by performing data entry, scanning and uploading PDFs, etc. In truth, many existing tools can help make the process easier. Making something digital in the first place—using a short sign-in form that automatically populates the results into a database—instead of transferring something from analog to digital, saves your party time and is more efficient.
If you have existing Excel sheets, most CRM tools and ESPs allow you to upload Excel sheets and comma-separated values (CSVs) directly to their databases. As part of the upload process, they will allow you to match the fields in your datasheet with those that exist in your database.
Additionally, in cases where the data exists in a file format other than CSV, such as a PDF document, there are tools that will assist in converting and formatting it into a CSV that can be used for your database. For example, historical voter rolls may exist solely in PDF. By converting the file into a CSV, you can upload the data and enrich the database. Some popular examples of these tools include Adobe Acrobat, DocParser, Tabula and PDFConverter.
With digitized data, there is always a risk that a system could crash or data could otherwise be lost. For this reason, you should always have backups of data stored in a separate location. For more information on backing up data, please refer to this resource.[11]
[11] “How to Back Up or Transfer Your Data ono a Windows-Based Computer,” Microsoft. Accessed 17 Aug. 2022, support.microsoft.com/en-us/topic/how-to-back-up-or-transfer-your-data-on-a-windows-based-computer-bd7e1bcf-15ea-078b-922f-6d6fcca76c7e.
How to Organize Your Data
Spreadsheets
Spreadsheets, like those created in Microsoft Excel, are the simplest solution for managing campaign data. The benefits of spreadsheets are that they encourage a disciplined approach to campaign data collection, creating standard fields such as contact information, participation history and other relevant details. Additionally, spreadsheets can be easily sorted, searched or filtered—getting exactly to the data or subset that is useful.
Cloud-based spreadsheets, such as Google Sheets, allow all members of the campaign team to work from the same version of the file, which traditional Excel files do not enable. Updates made by one team member can be easily referenced and immediately seen by others, and all members of the team have access to the most up-to-date version of the data.
Whether using traditional spreadsheets or cloud-based versions, it is important to consider the best way to secure the data contained within. Both versions have the ability to define which users have access via passwords or access protections. When deciding how to secure the spreadsheet, it is worthwhile to balance the sensitivity of the data with the need to have more team members able to access it.
Customer Relationship Management Software
As a campaign grows, so does the amount of data collected. The number of spreadsheets will become too large and unwieldy.
This is the stage at which a stakeholder relationship management software, otherwise known as a customer relationship management platform, becomes useful. A CRM is a software application that centralizes your data so that it is more searchable and actionable, and better able to integrate with voter-contact tools such as email, texting, and advertising.
Some of the advantages of a CRM are:
- A centralized data source in which different lists can exist together while continuing to maintain strong security standards.
- As the market has grown, more tools have become available that are both cost effective and user friendly.
- Many CRMs have the built-in functionality to integrate with common voter-contact tools, such as Mailchimp, peer-to-peer (P2P) texting or Facebook advertising.
- Customizable access tiers ensure that staff and volunteers have access only to the data and features they need, without exposing the campaign’s entire database.
- Many CRMs include analytics dashboards to track and measure the campaign’s performance and growth.
Recommendations for CRM Software
Ensure that your party regularly backs up the data stored in a CRM and regularly exports it, to ensure that you own the data and that the data is not trapped in the CRM. Your data should be accessible and able to move to another database or CRM. If you cannot pay CRM fees for a few months, make sure you do not lose access to your data if you lose access to the CRM; keep your backup data stored as an Excel file in a folder in a separate location. Name the file “FILE NAME Backup DATE,” and only access this file if you lose the original data.
Advanced Data Solutions
Beyond a certain size, it may become too expensive (most CRMs will charge according to the size of the data hosted on their servers) or too unwieldy to rely solely on a CRM solution. In these cases, such as when a party has reached national stature, it is worth exploring enterprise-level, cloud-based, data-storage solutions such as Amazon Web Services (AWS) or Microsoft Azure. This level of data management is typically beyond the scope of a general party staffer and should be the responsibility of an experienced data director, IT officer or trusted third-party vendor.
Transferring Your Online Data
Advanced File Sharing and File Transfer Protocol
FTP provides a method for transferring data across the internet between users who have been granted access via secure credentials. If you are interested in learning more about this solution, please see the following resources.
For more information on TFPs, please refer to these guides:
Data Portability
Finding the right technology products for your organization may involve some trial and error. After experimenting with a particular product, some organizations may find they need a tool that offers more features, provides an easier user interface or better meets their budget.
In those cases, it may be necessary to easily move data from the old tool to a new one. This capability is referred to as data portability, and refers to the ability to move data from one platform or service to another. It requires that data be stored in a commonly recognized format (e.g., .csv or .xls) and that the customer has the ability to easily export that data. Refer to this guide for more information on data portability.[14]
Before committing to any product, ensure you will be able to easily export your data for future use if and when you decide to stop using the product. This should be part of the conversation with any sales representative, or explored in the product’s documentation, before committing to a product.
The European Union has taken a proactive measure regarding data portability with its General Data Protection Regulation (GDPR), which requires data owned by users to be portable, and that electronic businesses and services must provide it to users upon request.[15] This is referred to as the “right to data portability.” Check to see if this regulation applies to you, or if your country has similar requirements. For more information on GDPR, see this report.[16]
[12] “What Is FTP: FTP Explained for Beginners.” Hostinger Tutorials, 10 Mar. 2022, hostinger.com/tutorials/what-is-ftp.
[13] Levine, Nicole. “How to Set up an FTP between Two Computers.” wikiHow, 28July 2022, wikihow.com/Set-up-an-FTP-Between-Two-Computers.
[14] “What Is Data Portability?” Talend. Accessed 17 Aug. 2022, talend.com/resources/what-is-data-portability.
[15] “Preparing for GDPR.” Talend. Accessed 17 Aug. 2022, talend.com/resources/gdpr.
[16] Exposito-Rosso, Stephanie, et al. “GDPR Data Portability: The Forgotten Right.” ALIAS. Accessed 17 Aug. 2022cellar-c2.services.clever-cloud.com/alias-code-is-law-assets/static/report/gdpr_data_portability_the_forgotten_right_report_full.pdf.
Core Function III: External Communications
Along with reaching your target audience, external communication methods are critical for informing voters about your party’s core values. Establishing and regularly communicating core values is crucial for your political party’s development and should serve as the foundation of your external messaging and party platform.
This section includes guidance on the following topics:
- Key components for effective digital communications
- Building trust
- Crisis communications
- Combatting misinformation, disinformation and hate speech
- Developing a social media strategy
- Digital communication tools
- Your party website
- Social media tools
- Digital advertisements
- Tracking engagement of members and supporters
- Campaigning and using databases for campaigning
What Is the Ladder of Engagement?
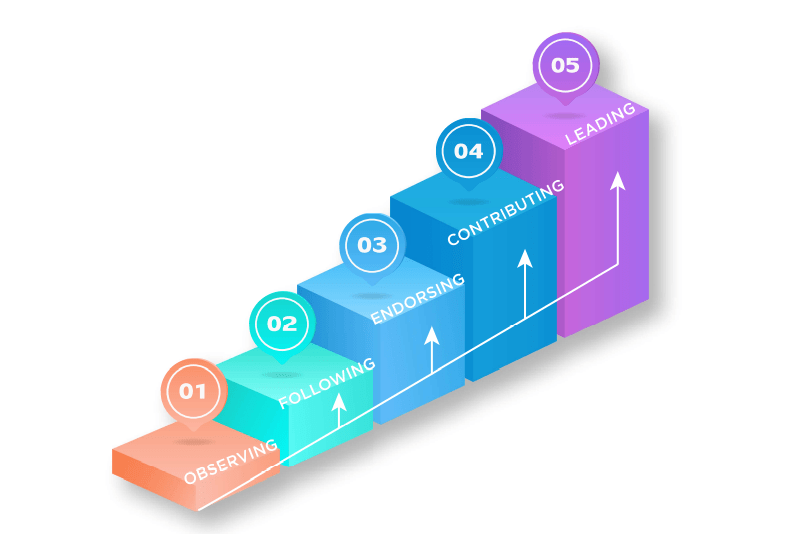
| Observing | The audience is just becoming aware of your party. Goals at this stage include building name recognition and identity with signage, online display ads, etc. |
| Following | The audience wants to know more. What do you stand for? What are your priorities? |
| Endorsing | This is the most significant step. The audience has made the mental leap from being outside the party to becoming a participant in it. |
| Contributing | The audience has decided that your party is not only worth supporting, but worth investing in with time or money. |
| Leading | The audience now sees itself as part of the party and a member of your community. It is looking to take responsibility within the party and be a catalyst for growing it. |
Over the course of this playbook, we will regularly refer to the Ladder of Engagement and reference the different stages as they relate to your online audience, as well as providing strategies to advance it along its journey.
The remainder of this section will include guidance on the following topics:
- Key components for effective digital communications
- Building trust
- Crisis communications
- Combatting misinformation, disinformation and hate speech
- Developing a social media strategy
- Digital communication tools
- Your party website
- Social media tools
- Digital advertisements
- Tracking engagement of members and supporters
- Campaigning and using databases for campaigning
This section will help you to develop a social media strategy as a component of your communications plan and will explore digital tools that your political party can use to augment more traditional forms of communication.
The first and most important step in establishing an external communications process is understanding and practicing the key components for effective digital communications, including building trust with voters online.
Key Components for Effective Digital Communications
Developing an effective digital communications strategy requires first establishing one key thing: trust. The trust that more traditional communication methods automatically build through in-person interactions must be intentionally developed when communicating online. The following sections provide recommendations for how to develop trust with voters online in order to make your digital communications effective, with particular guidance on how to do so in the context of a crisis or when facing misinformation and disinformation.
As mentioned previously, establishing a well-structured communications team can help your political party maintain trust and consistent communications with your target audience.
- Your party should have a director of communications, or at least a designated person who leads communications that will promote your party’s brand and strategize your party’s presence online.
- The director of communications should lead a broader communications team that will monitor media outlets and the press for relevant news updates and party references.
- The communications team will be responsible for social media and online activity. Your communications team will determine your political party’s approach to social media and will develop a social media strategy, which should be developed prior to posting online in order to take a strategic approach.
How and Why to Build Trust Online
Data Application Opportunity
Using your existing data tracking supporter and voter interest areas, you can more effectively personalize messages, invite feedback on specific issue areas and build trust on topics that are core to different segments of voters based on your contact database(s).
It is in the best interest of your party to establish a reputation of trust in all of its communications. Communications that are deceitful can hurt your party’s reputation and can cost votes in the long run. Therefore, it is essential for your party’s communications to be established in truth to build trust, to ensure your messages resonate and that your communications are effective. Here are some key points and actionable steps for your political party to consider when building trust online.
- Be open and transparent. Especially when engaging in campaigns, your voters will want to know about your party and its members who are running for office. Being open with your audience allows your party to form genuine connections.
- Meet your voters where they already are. Build familiarity with party supporters and voters by using the communication channels with which your community feels most comfortable and familiar.
- Listen to your audience and personalize engagements. Your campaign can use breakout rooms in online meetings to facilitate a more profound dialogue between you and your audience members. Use first names when possible and reference specific things you have in common—neighborhoods, families, etc.
- Create opportunities for feedback. Use chats and polls during virtual engagements to make your audience feel heard and to elicit feedback.
- Tell authentic stories with which your audience can genuinely relate, in order to form a personal connection.
Building trust, especially online, is an ongoing process that feeds into all aspects of external communications and is critical to your political party’s work and overall reputation. Maintaining consistency in your messaging, communicating clearly and keeping your core values at the heart of your messaging—along with sustaining the recommended practices listed above—will sustain trust in the long term. For additional guidance on building trust, consider reviewing this resource.[17]
Data Application Opportunity
[17] Pradhan, Sanjay. “An Open Government Approach to Rebuilding Citizen Trust.” Open Government Partnership. Accessed 17 Aug. 2022, opengovpartnership.org/trust/an-open-government-approach-to-rebuilding-citizen-trust/.
Crisis Communications
Data Application Opportunity
Along with building trust, your party’s data can greatly strengthen your crisis communications. You can easily sort segments of your contact database who might be more vulnerable to a crisis due to their location or other tracked information. You can easily export contact information for individuals in your email or Short Message Service (SMS) lists who may be more clearly affected by the crisis.
During unpredictable or politically contentious times, citizens—including your members and supporters—will look to your party to be a calm, clear source of stability and information.
Digital tools can be useful for amplifying messaging during a crisis, including disseminating information to members more widely, efficiently and interactively. Remember inclusion principles whenever you’re incorporating digital tools and remember that digital communications should amplify, rather than replace, more analog messaging—especially during a crisis.
Case Study: Trust in Germany during COVID-19
Throughout crisis communications, use the following seven elements of effective messaging to ensure the party serves as a clear and consistent voice of authority:
- Focus on facts: Include clear, unbiased data and statistics throughout your communications to indicate the party is providing informed guidance and information based on objective and evidence-based sources.
- Express empathy: Including empathy throughout your communications lets voters, members and supporters know the party is leading with its community in mind. Try to emphasize empathy even in short digital communications.
- Communicate with consistency: Party communications should come from a clear and consistent source or set of individuals. For political parties, this should most likely include senior party leaders such as the communications director. Remember to remain consistent with the digital platforms you use.
- Detail the action(s) being taken: Sharing the action(s) the party is taking to address the crisis provides transparency. Remember to give people information that will help them; panic and speculation in place of facts only add to a crisis.
- Follow-up and next steps: Tell your audience how to reach the party, its candidates and elected officials, and be sure to share what digital communication platforms exist. To set clear expectations, be transparent about any planned next steps, what the focus will be and how those next steps will be achieved.
- Recurring communication: Finally, tell your members when, how and at what frequency they can expect communication from the party, and clarify what method will be used. Will you use email or a press conference? Through what digital tools? Daily or weekly? Providing these details will create predictability in an otherwise uncertain situation.
Most important of all, never speculate. Remember it is okay – and often necessary – to express uncertainty. Although difficult, recognition of unknowns provides an opportunity to be transparent with members and citizens, and to reassure them that only reliable and honest information is being shared. Additional, step-by-step guidance can be found here at How to Create a Crisis Communication Plan, including a communication plan template.[18]
[18] “How to Create a Communication Plan Template.” CivicPlus. Accessed 17 Aug. 2022, civicplus.com/blog/ps/how-to-create-a-crisis-communication-plan.
How and Why Your Party Should Combat Disinformation and Hate Speech
Critical democratic processes, particularly elections, are increasingly targets of information manipulation by both foreign and domestic actors. It is necessary for your political party to be aware of threats to your party’s information environment during and outside of campaigns. Information manipulation is a set of tactics involving the collection and dissemination of information to influence or disrupt democratic decision-making, including misinformation, disinformation, propaganda, hate speech, etc. Such tactics can influence public attitudes or beliefs, persuade individuals to act or behave a certain way, or incite hate and violence. Information manipulation can also simply sow enough doubt or skepticism to make citizens apathetic; they may not turn out to vote and/or may stop supporting activities to advance your party’s goals. This threat should be a primary concern for your party, as the strategic deployment of false, misleading or disruptive information can bring chaos to countries and their political systems—and can undermine your party’s efforts to communicate a candidate’s stance or mobilize around your party platform more broadly.
Information manipulation can make it more challenging for your party to understand and aggregate citizen interests and mobilize citizens around those concerns, which will complicate your party’s ability to effectively advance candidates for office and secure votes. Further, disinformation can reduce trust in democratic institutions, including in political parties, and that loss of trust can increase if your party is seen as complicit in, or even as capitalizing on, the spread of disruptive and false narratives.
It is your party’s responsibility to be a steward of good information. Your party members must understand how to identify and respond to content meant to influence, disrupt or falsely distort the information ecosystem, to better protect elections and your party’s ability to communicate with and mobilize citizens.
Acting as a steward of good information requires both identifying and actively combating the spread of information manipulation once it has been spotted. It may also be helpful to conduct opposition research to understand the misinformation being spread about your party and candidates to help inform how, when and whether to respond. See this guide for step-by-step instructions on how to do so, including guidance for understanding, identifying and addressing information manipulation.[19] Below is a short summary of tactics your party can implement to actively protect the information ecosystem around elections and beyond.
- Proactive communications: Before false narratives begin to spread, your party should use proactive communications to provide accurate, reliable, consistent and concise information regarding a campaign and/or elections. Again, admitting uncertainty is okay if you do not yet know the facts. Focus communications on sharing what the government and party are doing to organize and prepare for elections, refuting misinformation and disinformation about the electoral process or your candidates, and promoting facts about the basics of how, when and where to vote months before, and during, the elections.
Inclusion: Communicating to the Most Vulnerable
Remember that marginalized social and issue-focused groups are often the primary targets of misinformation and disinformation attacks. Be sure to implement a wide range of communications tools before, during and after elections. Make sure to diversify the channels and messages you use to reach a broader group of citizens and party members, including using non-digital communication channels.
- Report to government, social media platforms, fact-checkers and/or Election Management Bodies (EMBs). Once you’ve identified misinformation or disinformation, consider reporting the content to the platforms where it’s spreading, to fact-checkers and INGOs for assistance or, if they are trustworthy, to election-management bodies or government agencies in your country. Please refer to page 16 of Combating Information Manipulation: A Playbook for Elections and Beyond for detailed information on how to report and to which entities.[20]
- Strategic silence: Remember that not all information manipulation requires a response. Actively deciding against debunking a false claim is a tactic called strategic silence. If engagement levels with the claim are low, attention is not widespread, there is no demonstrated effect, or the claim is unlikely to have an impact on voter behavior or beliefs, it is unlikely the falsehood requires an intervention. Responding to every false claim can have the unintended consequence of accidentally amplifying misleading information and drawing unnecessary attention to the claims.
Key Tip: Avoid Amplifying False Information
Repeating false information to correct it can sometimes result in an increased belief in the false information. Your communication campaigns should focus on repeating accurate information without referencing the information you are trying to debunk. For instance, an effective campaign would say, “Election Day is XXX. Only trust information from official sources,” and not “Election Day is not XXX. Do not trust information from XXX.”
Key Tip: Identifying Information Manipulation Offline
Remember that information-manipulation campaigns can occur offline as well as through online platforms; mainstream media (such as television, radio and newspaper) are common vectors for the spread of false information, and you should keep the above tactics in mind when consuming and sharing information from offline sources as well. Be sure to verify the information you hear or see before sharing it with your trusted networks and party members. Because mainstream media sometimes have intentional biases, they can feature false information or “half-truths.”
How to Develop a Social Media Strategy
Regardless of the platforms you use to engage with your potential voters, it is important to develop a strong social media strategy to organize your communication effectively across multiple platforms. Your campaign’s larger communication strategy should include a social media strategy. Consider the following best practices.
- Use a social media calendar to plan content, remain organized and schedule posts days or months in advance. Between campaign announcements, statements, videos and photos, a social media calendar will allow you to visualize your posting activity and keep it up to date, as well as note key dates surrounding the elections when you would like to post. Ideally, your communications team should have one month’s worth of content planned in advance. This will also give your party greater flexibility to respond to breaking news.
- Use consistent branding that coincides with your larger campaign communications plan. This includes standardizing logos and images, which makes your social media accounts easy to recognize and verify. Most voters don’t have the time or resources to deeply research and understand policy issues, so the deliberate association of a consistent brand with a policy orientation helps citizens make decisions about participation more easily.
Case Study: Branding by U.S. Political Parties
Consistent branding in political parties can be seen in the United States with the Democratic and Republican Parties. Both parties utilize symbols (the donkey for the Democratic Party and elephant for the Republican Party) and colors (blue for the Democratic Party and red for the Republican Party) that make their messaging easily recognizable. Popularized in the 19th century, symbols like the donkey and elephant can still be seen today in both offline and online branding.
Keep the Ladder of Engagement in mind. Each interaction with voters is an opportunity to encourage them to engage more consistently or deeply with your work. Think about integrating varying calls to action throughout your posts and content—inviting donations, promoting volunteer opportunities, requesting reposts, etc.—to encourage voters to further invest in your political party and its work.
Digital Communication Tools
Data-Collection Opportunity
Your Party Website
Your website should act as a central signpost for your party online. It will serve as a way to explain your party’s mission and guiding principles, as well as a platform for external communications, contact information, email acquisition and donations. Many online tools can allow your party to create its website in an easy and inexpensive way. Some popular tools include Squarespace, Wix and NationBuilder. All of these services offer a drag-and-drop design interface so users can design their site without having any knowledge of computer code.
Furthermore, these platforms have built-in solutions for email acquisition, blog feeds, databases and integration with external communications tools such as email and social media. Beyond that, they typically have many easy-to-use integrations with popular third-party tools that link your site with your own preferred email service provider, databases, fundraising platforms, etc. Keep in mind that each tool will have different pricing options. Typically, the more time you invest in developing and maintaining tools, the more useful they will be.
If the significant levels of upkeep and technical know-how required for a party website are too intensive, an alternative way to communicate your party platform is to launch a well-organized Facebook Page to actively share your agenda and goals. Visit this website for instructions from Meta, Facebook’s parent company, on best practices to create a Facebook Page for political organizations and actors.
Your party website should include the following features, all of which should be easy to reach via a global header menu that exists throughout the site.
- About section: Typically found on the homepage or on a standalone page found in the header menu, the About section will provide a brief summary of the party’s guiding principles, who serves in party leadership and the party’s policy priorities.
- Donation page: Your donation page is the easiest way to convert interest in your political party into a donation. It should be easy to find—such as with a large, distinctly colored button on the homepage—and link directly to a page containing your donation-management platform.
Completing the donation page should be as seamless as possible to increase conversions on the page. Strategies for achieving this include: reducing required fields to the bare minimum necessary to identify the donor and meet local reporting requirements; offering suggested donation amounts; concise calls to action; and reducing unnecessary imagery or videos that could distract the user or cause the page to load slowly.
- Sign-up form: Create a clean, easy-to-use webform that collects important details, such as email, phone number and address, from those who are interested in becoming more involved with your party. The sign-up form should be integrated with a database, either on the website itself or through a third party, where the data will be housed after collection. The sign-up form should be on the landing page.
- Issues section: Include a clean list of issues and the party and candidates’ stands on issues. This should allow anyone visiting your website to quickly and easily understand the party’s position on various issues and topics potential voters care most about.
The above pages should be easily accessible from anywhere on the website, and the “donate” and “become a member” functions should have very visible buttons on every page of the website.
Additional resources you may want to include on your website include a social media feed, an events calendar, party resources, a blog, etc. The key is to ensure that as the content on your website grows, it remains easy to navigate for site visitors. When building a navigation menu, it is useful to prioritize the information that is most valuable for visitors.
Key Tip
Use your mobile device to review your website and test web forms or donation pages. If it is difficult for you to use the site on mobile, it will be just as difficult for the audience you wish to engage. Close to 60 percent of web traffic is conducted on mobile devices, and that number continues to increase.
Privacy Policy and Terms and Conditions
Most countries require websites that collect data to have a privacy policy, terms and conditions or both. These links can typically be found at the bottom of a website. The privacy policy is a statement of understanding between the owner of the website and visitors, disclosing that the site collects personal information such as the data collected from webforms or in the form of Internet Protocol (IP) data from the user’s device. Likewise, the terms and conditions disclose how the owner of the website intends to use that data in the future.
The regulation of privacy policies and terms of conditions is typically administered on a country-by-country basis, so it is necessary to research the requirements in your jurisdiction. For those who have not drafted these policies previously, it is also useful to explore what others have done in your local jurisdiction.
There are free online resources that can help organizations draft these policies, examples of which can be found at TermsFeed.com and FreePrivacyPolicy.com.[21]
[21] “Privacy Policies vs. Terms & Conditions.” TermsFeed, 1 July 2022, termsfeed.com/blog/privacy-policies-vs-terms-conditions; Page, Alison. “How to Write a Privacy Policy.” FreePrivacyPolicy, 1 July 2022, freeprivacypolicy.com/blog/write-privacy-policy/.
Website Analytics
An important and often overlooked benefit of your website are the back-end analytics, which provide important information regarding how visitors use your website. The analytics can answer questions such as:
- When are visitors visiting your site?
- What are the demographics and geographic breakdown of your audience?
- What sources are driving traffic to your site? Are they arriving from search results, social media, email or other sites?
- Do site visitors find the information useful by staying on the site, or are they leaving quickly?
While many websites offer their own website-analytics dashboard, Google Analytics is the mostly universally used solution—and free.
Google provides its own resources for walking you through the set-up process, and many website platforms offer their own step-by-step guides for integrating Google Analytics.[22]
- Integrating Google Analytics with NationBuilder
- Integrating Google Analytics with Squarespace
- Integrating Google Analytics with Wix
Pixel is a tool offered by Meta that you embed within your website. It allows you to better understand the actions people take on your website and measure the effectiveness of your advertising and outreach.
[22] “Get Started with Analytics.” Google. Accessed 17 Aug. 2022, support.google.com/analytics/answer/9306384?hl=en.
Search Engine Optimization
An overwhelming majority of your site visitors will arrive at your site from a search results page, such as a Google results page. Search engine optimization (SEO) is the practice of increasing your site’s web traffic by improving your ranking in search engine results. Web pages with higher rankings will appear more frequently in search results, which leads to increased traffic.
The algorithms that guide search results are designed to help users find the most relevant and useful information. By following SEO best practices when designing your website, you can take active steps to ensure that the search results are connecting you with your supporters.
- Create a unique search-friendly title for your website, such as the name of the party or other commonly used monikers. Employing a distinct and descriptive header will allow your site to stand out among crowded search results.
- Make sure your pages follow a proper hierarchical structure. For example, if your About page includes subpages on party leaders, those page uniform resource locators (URLs) should be constructed as follows: website.com/about/party-leadership.
- Be aware of commonly used keywords and use those in your page titles, headers and search engine page descriptions, and frequently in the body copy.
- For example, a Green Party may want to prioritize keywords such as: “environment,” “sustainability,” “clean energy,” etc.
- Your website analytics dashboard will often include the search terms that are driving visitors to your site. Reviewing your analytics dashboard can provide insight on additional keywords that you should include.
- Search results prioritize websites that are authorities on particular subject matter. Seek to write authoritatively on key topics for your party. This can be accomplished in your About section when outlining your guiding principles, or on your blog when discussing policy issues in depth.
- Make your content easy to digest and at a reading level accessible for the average user. Try to simplify topics for an audience that will likely have limited familiarity with the subject matter.
- Link to other relevant and authoritative websites, such as news publishers and government web properties.
Social Media Tools
Data Application Opportunity
This is an opportunity to take the data you have and use it to conduct effective and efficient outreach to supporters and potential supporters. Use your data to generate outreach lists for specific groups, such as groups segmented along issue areas, demographic lines or individuals best reached via specific tools like Facebook.
In addition to a party website, social media tools are key resources to use as you expand external communications online. The below list includes various social media platforms that will be useful in your party’s external communications, as well as a brief explanation of each platform and its key features that can be especially useful in the context of a campaign.
When using social media tools, always ensure you are complying with their rules and regulations, as well as any local laws. Take time to understand what data the tools are collecting on your supporters and how they intend to use it.
It should be noted that social media accounts offer an excellent opportunity to collect data for your party’s purposes. Users who respond to your content will often be interested in receiving your newsletters, attending events, receiving breaking news, etc. To that end, social media is useful to frequently and consistently link back to data and donation-collection forms your party manages.
The tools selected in this list were chosen based on their widespread use in external communications globally. As you develop your social media strategy, be aware of the platforms popular with your target audience, as use varies based on demographics, specific communities and levels of connectivity and access. See Annex B for guidance and considerations on inclusion throughout your party’s efforts.
Finally, keep the Ladder of Engagement in mind as you conduct communications through social media and other digital tools. Consider varying your use of features integrated into each platform to encourage observers to become followers, and to then graduate toward higher levels of engagement through varying calls to action.
At the time of this writing, the below information on the platforms and their available features is accurate. However, given rapidly evolving changes at the platforms, please refer to their help centers for the most up to date information and remain wary of new security concerns.
At the time of this writing, the below information on the platforms and their available features is accurate. However, given rapidly evolving changes at the platforms, please refer to their help centers for the most up to date information and remain wary of new security concerns.
When utilizing Facebook, it is critical for your party to have a single official party Facebook account, as well as separate accounts for individual party candidates. This is necessary to keep information about your party separate from that of volunteers’ personal accounts, as well as separate from the personal accounts of candidates. An easy way to protect your party’s information and presence on Facebook is to enable two-factor authentication, a mechanism that strengthens your security by requiring two methods to verify your identity, rather than a single password.
There are two distinct ways to have a presence on Facebook: Profiles and Pages.[23] Profiles are best for individuals and candidates. Pages are best for the party as a whole, as they enable you to connect with supporters en masse. When someone likes or follows a Page on Facebook, they can start seeing updates from the Page in their Feed and remain connected to party news. You will need a Profile to set up a Page, and the individual with that Profile will manage the Page.
- Campaigns should communicate through a Facebook Page. This gives you a public presence to connect at scale with people who your party may or may not know personally. Pages provide tools such as insights to track engagement metrics, civic-engagement tools, mobile apps and the option to advertise. Take a look at Facebook’s guidance on best practices for political organizations.[24]
- Political parties can also advertise on Facebook. In many countries, your party must follow Facebook’s authorization process to use this feature.[25] Facebook offers a variety of ad options including image, video and call-to-action ads. Refer to this resource to better understand what is required in your location.[26]
- Call-to-action ads can elicit a response from the viewer to sign up, connect, learn more or watch a video. When making a call-to-action ad, be direct and unambiguous. Make clear what steps you would like the user to take next.
- Meta Business Suite allows your political party to see your posts’ performance, track trends and learn more about your Facebook audience.[27]
- Follow the advertising regulations and laws in your country, as well as Facebook’s policies related to advertising.[28]
[23] “Your Profile.” Facebook. Accessed 17 Aug. 2022, facebook.com/help/396528481579093/?helpref=hc_fnav; “Create a Facebook Page for Your Business.” Meta. Accessed 17 Aug. 2022, facebook.com/business/help/473994396650734?id=939256796236247.
[24] “Best Practices for Political Organizations.” Meta. Accessed 17 Aug. 2022, facebook.com/gpa/best-practices/political-organization.
[25] “Get Authorized to Run Ads About Social Issues, Elections or Politics.” Meta. Accessed 17 Aug. 2022, facebook.com/business/help/208949576550051?id=288762101909005.
[26] “Availability for Ads About Social Issues, Elections or Politics.” Meta. Accessed 17 Aug. 2022, facebook.com/business/help/2150157295276323?id=288762101909005.
[27] “Meta Business Suite.” Meta. Accessed 17 Aug. 2022, facebook.com/business/tools/meta-business-suite.
[28] “Information on Prohibited Ads Related to Voting and Ads About Social Issues, Elections.” Meta. Accessed 17 Aug. 2022, facebook.com/business/help/253606115684173.
Instagram offers a visually compelling way to engage audiences through photos, videos, stories and messages. Utilizing a “Creator” account offers a unique profile appearance and more advanced user insights to better track engagement. As with Facebook, candidates, members and your political party should have separate accounts. Instagram provides various methods to share content and messaging including the following.
- The Feed is the place to post content you want to remain permanently visible on your profile and appear to people scrolling through their timelines.
- Stories remain visible for 24 hours and can be used to broadcast live Q&A sessions, interviews and campaign events.
- Direct messaging works as a private messaging inbox where you can receive one-on-one messages from your followers.
- IGTV is used to post long-form videos, up to 60 minutes long. This is ideal to post full-length speeches.
- Reels are used to record and edit 15-second multi-clip videos with audio, effects and other creative tools. These can be shared on your Feed or can be made available to more Instagram users through the Explore feature.
- Instagram Insights can track engagement and day-by-day progress, including a detailed overview of how and why your account grows (or does not grow) each day in a given week, and how many follow and unfollow your account receives.
- Instagram offers a variety of advertising opportunities including photo, video and Stories ads. As with Facebook, you must complete an authorization process to run ads in certain countries.[29]
For further guidance on how to utilize Instagram and its guidelines, please view Instagram and Politics & Government and Community Guidelines. [30]
Twitter is a great platform for short interactions that allow for direct contact between campaigns and their followers. Twitter messages, primarily designed for mobile phones, allow users to create tweets limited to 280 characters. Twitter is useful for sharing the latest campaign announcements and elections information, and promoting your campaign efforts, including the promotion of services and events. A tweet can be used to share messages, a link, a photo, a video or a combination of all four. Some other key features of Twitter include the following.
- Direct messages allow you to start a private conversation or a group conversation with anyone who follows you. This can be useful for your campaign to directly connect with your audience.
- Twitter Live lets you share live videos from campaign events to better inform and connect with your followers.
- Lists can be used to organize and read tweets from selected groups, allowing you to keep track of what groups are saying. Lists can be useful for political parties to follow tweets from their own party or other members.
- Twitter analytics allow you to measure your tweets’ engagement and learn more about your followers, and include other tools.
- Note that, at the time of this writing, Twitter prohibits political advertisements and the promotion of political content.
Utilizing hashtags for your party can help boost viewership and allow you to more closely and frequently connect with conversations surrounding your party. For more guidance on using Twitter, please view the Twitter Manual for Governments and Twitter’s regulations on political content. [31]
[31] “Twitter Manual for Governments.” Government of Catalonia. Accessed 17 Aug. 2022, onthinktanks.org/wp-content/uploads/2017/06/Twitter-Manual-for-Governments.pdf; “Political Content FAQs.” Twitter. Accessed 17 Aug. 2022, onthinktanks.org/wp-content/uploads/2017/06/Twitter-Manual-for-Governments.pdf.
YouTube
YouTube offers an accessible platform to engage with your party followers on what’s currently happening in your campaign through video. YouTube allows you to create a channel where you can upload videos, create your content and live stream events. Services include the following.
- A brand account allows your party’s communications team to manage editing permissions, create your online presence and grant access to the account to various party members.
- YouTube Live allows your party to broadcast live content and allows your audience to participate with real-time comments, questions and reactions. Your party can live stream through a webcam, mobile camera or encoder streaming.
- Your party can advertise on YouTube through GoogleAds. There are a variety of ads you can post on YouTube, including non-skippable and skippable video ads before videos, bumper ads and sponsored cards. Here is more information on YouTube Advertising.[32]
- YouTube Analytics can help your party understand your channel’s performance, reach, engagement and audience.[33] Be sure to follow your country’s policies alongside YouTube’s Community Guidelines.[34]
[32] “Grow Your Business with YouTube Ads.” YouTube Advertising. Accessed 17 Aug. 2022, youtube.com/intl/en_us/ads.
[33] “YouTube Analytics Basics.” YouTube Help. Accessed 17 Aug. 2022, support.google.com/youtube/answer/9002587?hl=en.
[34] “Community Guidelines.” YouTube Help. Accessed 17 Aug. 2022, youtube.com/howyoutubeworks/policies/community-guidelines/.
TikTok
TikTok is a video-sharing social network that your party can use to create videos to engage with its users. Videos on TikTok can range from 15 seconds to three minutes and can feature sounds, effects and text. You can also share videos and chat with others through its messaging feature. TikTok for Business can provide your party with resources, analytics, guides and best practices to reach your audience.[35]
- TikTok prohibits political ads, including ads that promote positions on issues of public importance.
- Security note: There are concerns about the safety of TikTok in regard to privacy. TikTok collects information on its users’ usage, device, location, metadata and cookies. In addition, there is no end-to-end encryption on messages. As with any social media platform, be sure to consider these risks as your party considers social media tools.
[35] “Ads that Entertain. Campaigns that Connect.” TikTok for Business. Accessed 17 Aug. 2022, tiktok.com/business/en.
WhatsApp is a messaging application that allows for messaging, internet voice and video calling, and document sharing on both your mobile phone and desktop computer with end-to-end encryption. According to Meta’s rules, political parties are unable to use the WhatsApp business app. Note that sending WhatsApp messages to users without permission can lead to your party’s accounts being banned from the platform.
Signal
Signal is a free, end-to-end encrypted messaging platform that offers voice and video call features. Signal is free to use and functions across mobile and desktop platforms (on Android, iOS and Chrome) with features including group messaging, private messaging and high privacy standards. Signal is recommended for sensitive communications between individuals and groups. For the most up-to-date information about Signal, please visit Signal’s website.[36]
[36] “Speak Freely.” Signal. Accessed 17 Aug. 2022, signal.org/en.
Telegram
Telegram is a messaging app that can be used on phones, tablets or computers, allowing for voice calls and the creation of group messages for up to 200,000 people. Telegram features similar to those of WhatsApp and Signal. However, due to its lack of automatic end-to-end encryption, there are security concerns around most of Telegram’s services (see below for more information). Services include the following.
- Telegram Channels can broadcast information to a large audience that can be either public or private. If the channel is public, it can be searched and found by anyone. This is a great way to share speeches or events. Only one-way communication is possible in a channel; participants cannot respond.
- Groups allow for two-way communication between organizers and group members. Group messages are ideal for smaller, more targeted groups, although they can allow for 200,000 members.
- Security Note: It is important to consider the potential risks in using Telegram. Telegram only allows end-to-end encryption when Secret Chats are enabled—unlike WhatsApp, where end-to-end encryption is automatically enabled across features. Group chats are also not encrypted on Telegram. Telegram’s cloud-based server gives Telegram access to any data that you store on the cloud.
- Telegram prohibits advertisements promoting political campaigns, elections, political parties, movements and candidates.
Text Messaging/SMS and P2P Texting
SMS messages allow your party to reach anyone who has a mobile phone. Using SMS allows your party to send short updates or urgent information, and to send that information in bulk. Remember to check local regulations around bulk messaging. In addition, these messages allow for real-time and two-way communications with members and supporters. Be sure to use clear, concise and personalized messaging to avoid having your messaging confused as spam. Simple SMS messages can be useful for reaching individuals without access to smartphones or computers and require very little internet bandwidth for those in low-connectivity areas. They also have very high “open” rates, often more than any other type of contact.
If you wish to initiate one-on-one conversation with the numbers you text, you can use peer-to-peer messaging rather than sending a bulk SMS blast. P2P texts are another way your party can reach those with a mobile phone. In contrast to standard SMS messages, which let you message a list of people at once, these messages are sent one at a time so that you can reach people who have not previously opted in to receive texts from your organization.
Email messages can be used to send longer and more detailed information to your party members, and can be used to send customized information at little cost. Your party should have a variety of email accounts, including a general account, one for campaigns and separate accounts for individuals. This will allow you to send certain emails from specific accounts. For instance, this can allow your party to send campaign emails from a campaign-specific account. In addition, your party can utilize shared mailboxes that allow you to have one place from which mail from separate accounts comes.
Your party can send emails directly from your email account or you can use an email marketing service such as MailChimp, which allows you to send email campaigns to specific audience lists at specific intervals. An email marketing service gives you more tools than a standard email account. You can see analytics, conduct A/B testing and import a CRM, among other benefits. However, services like this are more expensive than free email accounts.
Email campaigns can inform party members about upcoming events, build awareness of an issue, inform party members of the latest news, disseminate an online survey, share specific resources or fundraise. Emails should always include a clear call to action (CTA) and a mechanism that helps voters take action as easily as possible. A listserv, an application that distributes messages on an electronic mailing list, can be used to store and maintain email addresses and allows for the easy dissemination of mass communications. (See page 14 in the Internal Communications section for additional guidance on listservs.)
However, you should not solely rely on email to communicate, because many people neglect checking their email. To reach the broadest group of people, use multiple tools to share the same message.
Digital Advertisements
Advertising is a critical communications tool that can be used to connect with individuals, get your messaging across and garner support for your party. To reach the broadest segment of the population, your party should consider digital forms of advertising, in addition to analog media such as print or radio advertising. Digital advertisements have become an increasingly critical component of political parties’ external communication plans and are an effective way to promote your party on social media, websites or even search engines. Refer to the above list of communication tools for specific links and advertising guidance for each platform.
Message Testing
In creating digital advertisements, it is important to use audience segmentation, the process of dividing individuals into homogeneous groups based on certain criteria. For example, advertisements can target people based on gender, social interests or age. Audience segmentation allows your political party to customize its content toward a particular group based on certain characteristics such as geography, age or other demographics. This is key to the success of digital advertisements, as different groups may be interested in different topics. For instance, your political party can use digital advertisements to target younger members of your community to inform them about voter registration or educational resources about the political system.
Advertising Strategy
Each advertising campaign should be designed with a specific goal in mind.
- Goal: Awareness. As with a consumer brand, the goal is to increase the campaign’s name identification. Awareness ads are designed to give audiences an idea of what the campaign is and what it stands for, often making an emotional appeal. Static display ads, such as those found on news sites, and video ads are often effective for awareness campaigns.
- Goal: Acquisition. Acquisition campaigns are designed with the specific purpose of gaining data, typically contact information such as an email, phone number or address. Collecting this information allows the campaign to engage with this supporter more cost-effectively in the future. Because social networks are designed to encourage a response from audiences, they are particularly well suited for acquisition campaigns. Facebook even has an ad unit specifically designed for lead acquisition, which publishes guides to help you conduct effective acquisition campaigns.[39]
- Goal: Getting votes. In the final stretches of the campaign, the focus changes from convincing the electorate to turning supporters out to vote. At this stage, it becomes important to ensure that your supporters have important information about when, where and how to vote. If your party has especially strong data, you may be able to simultaneously allocate resources to mobilize weak supporters and persuade undecided people, but you first need to know the difference.
[39] “Generate New Leads by Providing Value for People.” Meta. Accessed 17 Aug. 2022, facebook.com/business/ads/lead-ads.
How To Set Up An Advertising Account
Many popular advertising platforms, such as Facebook and Google, have online resources for information about setting up an advertiser’s account. The following links provide additional information for setting up an advertising account.
It is worth noting that platforms such as Facebook and Google require political advertisers to become authorized to run ads related to political elections and other social topics. These authorizations are intended to ensure that advertisers are who they say they are, and that there is greater transparency for the general public about who is running the ads.
The specific steps for authorization and transparency can vary by country, so it is worthwhile to explore the platform’s resources to ensure you are meeting all local guidelines.
Ad Platform Comparison
| Direct from Publisher | Video | Audio | |||
|---|---|---|---|---|---|
| Target Audience | Social Media Users, Large Audience Base | Information Seekers | News Readers | Internet Users Across All Channels | Internet Radio Users |
| Networks | Facebook News Feed, Instagram | Display, Search, YouTube | Display, Video, Sponsored Content | YouTube, Social Media, Streaming TV Services | Spotify, Pandora, iHeartRadio |
| Accepts Political Advertising | Yes | Yes | Yes | Yes | Yes |
| Optimal Advertising Tactic | Acquisition, Direct Response | Awareness, Direct Response | Awareness | Awareness | Awareness |
| Video | Yes | Yes, YouTube | Yes | Yes | In certain cases, video units can accompany the audio ads. |
Digital Advertising Best Practices
Data Application Opportunity
Much like the digital tools listed above, advertising outreach should be informed by existing data tracking key issue areas, demographics and other supporter and voter information to help create ads that will resonate with your supporters and potential supporters.
- Use attention-grabbing visuals to encourage people to stop scrolling and read your content.
- Utilize heavy text overlay, otherwise known as subtitles, because many digital ads are viewed with the sound off. For example, 85 percent of Facebook videos are viewed with the sound off.
- During the ad creation process, think about how the ad will be viewed on the specific platform. A 30-second ad may work better as a pre-roll ad (a short sponsored video that precedes the user’s chosen video) on YouTube, whereas a shorter video may work better in a social network feed where attention spans are limited. Consider design questions such as whether a dynamic display ad with attention-grabbing movement or a static display ad is optimal.
- Don’t stress too much over video production quality. Simple video filmed with your mobile phone performs well on digital platforms because it is personable and authentic. Your party will need to determine the right tradeoff between production value, cost and authenticity.
- Pay attention to technical requirements. Most advertising platforms have specific requirements in terms of pixel dimensions and file size, which they should provide to you as part of the buying process: horizontal or square for Facebook, square for Instagram feed, vertical for Instagram stories, etc.
- Include explicit calls to action, available either consistently or at multiple points in the ad.
Key Tip: Get to the Point
Attention spans are short, particularly if your content exists in a social media feed where users are mindlessly swiping. In order to be effective, it must grab the user’s attention immediately and get your central message across early. Regardless of the platform, you are likely to see viewer drop-off after just 15 seconds.
Tracking Engagement of Members and Supporters
Most political parties have limited resources—such as time, money and staff—to dedicate to membership management and engagement. Digital tools can be key to helping you understand interest, engagement and the priorities of your members and potential supporters, and can help you identify what demographic and geographic groups may respond to your party’s message through effective outreach.
Tracking engagement with your party’s external communications can not only help inform the demographic and geographic groups most receptive to your message, but it can also help you understand what values and issue areas most resonate and which voter-outreach methods are most effective. Tracking engagement with social media posts enables your party to learn about voters’ issue priorities in real time and adapt your external messaging accordingly.
It also helps you determine what tools are most effective in terms of money spent per vote. When considering using outreach and advertising methods, think for example about how many marginal votes you are producing per dollar via hiring canvassers, versus spending those same dollars on producing a series of digital ads. You need to experiment to figure out how to spend that money most efficiently.
The vast majority of online campaign tools have an analytics dashboard section that allows you to track the performance of your efforts. These dashboards can be extremely useful in determining which tactics and campaigns have been effective and which should be discarded.
In some cases, the amount of available analytics can be overwhelming. If this is the case, it is important to align the campaign’s objective with the relevant metrics. For example, an acquisition campaign can be judged on the cost per new email acquired. On the other hand, an awareness campaign could be judged on the cost to achieve 1,000 impressions.
One of the advantages of digital advertising is that it allows organizations to easily test multiple ad variations with different copy, visuals or messages. The performance of those campaigns can then be compared to determine which messages are best resonating with your audience.
These important metrics are often referred to as key performance indicators (KPIs), indicators that evaluates the success of a specific activity. Some relevant KPIs for digital campaigns include:
- Cost per acquisition (CPA) or cost per conversion: What is the cost of investment for every collected email? This reflects how strongly the user values a future relationship with the political party.
- Click-through rate: The percentage of users from the overall audience who engage with your advertisement. This reflects the effectiveness of your initial pitch or call to action.
- Cost per like/cost per follow: The cost of advertising that leads to acquiring one new like or one new follower.
- Impressions: The total number of times your ad was seen by the online audience.
- Cost per 1000 impressions: Because the scale of a digital campaign can quickly become very large, even as high as tens of millions, marketers often break impressions into lumps of 1,000. The cost-effectiveness of different platforms can be compared by their cost per 1,000 impressions (CPMs).
Data-Collection Opportunity
As you track engagement using your various digital tools, remember it is also an opportunity to collect information such as the gender, religion, ethnicity and political views of those engaging with your message. At every touchpoint, there is an opportunity to collect data about potential supporters, and you can strive to always offer an opt-in option for individuals to select to join regular communication lists and provide contact information such as their phone numbers and emails. Surveys are another method to expand data collection.
Campaigning
Managing political campaigns is a core operation for political parties and follows the same principles and best practices as external communications, explained in detail above. Campaigning is the method by which your party communicates with and persuades voters to support your party and candidate(s), and is ultimately the process by which your party platform and selected candidates are elected. There are a variety of techniques to reach voters and deliver campaign messages, an increasing number of which are digital. The tools and best practices referenced above are directly applicable to managing a campaign—especially considering campaigning is a form of external communications—and we recommend referring to the full external communications section for best practices and resources to help you campaign effectively.
Below we’ve included specific digital tools that might help your party identify the best opportunities to integrate digital resources into your campaign process, focused on the task of managing voter outreach and information during a campaign.
Databases for Campaigning
The ultimate goal of campaigning is to deliver your party’s message to effectively reach and mobilize voters. A core piece of this effort requires the organized management and tracking of potential voters. As campaigns integrate technology, voter contact is no longer a touch-and-go process, and neither is the management of voter data. Phone banking, canvassing, mailing and other communication methods have advanced to allow for finer data collection, voter tracking, segmentation and targeting through digital tools.
As your party shifts to campaigning online, developing a digital database should be your top priority. We have pulled out a few examples of available tools, including simple lists and more advanced CRMs that offer segmentation capabilities, allowing your party to group contacts who share characteristics and similar behaviors. For a fuller list of digital tools specific to campaigns, take a look at Political Campaign Tools: Running a Digital Campaign.[42]
- Simple lists: Good campaigns start with good lists. You can use simple tools such as Excel or even an organized Word file to develop simple voter-tracking lists to identify who your campaign has engaged and with which voters to communicate, and can develop distinct lists based on message type and intent. You can, and should, develop lists not just to track voters, but also to maintain contact information for volunteers, staff and supporters. As described earlier in the playbook, basic pieces of information to collect include voter name, physical and mailing address, party affiliation, contact information (such as email or phone number), contact history (did someone knock on the door, were they called, emailed, etc.), donation history and voting history (if available). Tracking voter information even with a simple Excel list will enable you to send messages more easily and rapidly to voters and communicate with them via phone, in-person canvassing, mail, email or SMS.
- Using a CRM: More advanced digital tools can allow your party to do much more than just track voters and their contact information. They can enable your party to automatically tag and segment voters within your database, and can integrate outreach tools like emails and SMS messages to create a “one-stop” communication and management tool . Examples of frequently used databases with additional tools are listed below.
- NationBuilder is a complete CRM that helps leaders maintain relationships with their support base, volunteers, staff and more. You can create a database, reach out to contacts in the database and set up a website, email campaigns, social media integration and donation processing.
- Ecanvasser is a total campaign software, including elements particularly useful for building voter data through canvassing. It includes easy-to-use tools to manage a voter database and segmentation, captures information from the field and syncs it with the database.
- CallHub can be used to easily reach out, engage and build a voter database using phone data if text messaging is popular in your country or local context. This tool allows for personalized texts, broadcast SMS for reminders and alerts, and an option for voters to opt in as subscribers.
- As a reminder, integrating digital tools into your campaigning processes comes with security risks and concerns.
[42] “Political Campaign Tools: Running a Digital Campaign.” CallHub and Ecanvasser. Accessed 17 Aug. 2022, civisanalytics.com/wp-content/uploads/2018/12/Political_Campaign_Tools-Running_A_Digital_Campaign.pdf.
Core Function IV: Fundraising
What is Fundraising?
Many of the core operations of a political party require significant financial resources. While your party may receive some funding from the state, it is often not enough to conduct effective campaigns. All fundraising must be done in accordance with local legal regulations. Before starting a fundraising campaign, research and understand the local legal requirements and regulations you must follow. Fundraising is something that works everywhere—all countries have a tradition of charity and/or fundraising.
This section includes guidance on the following topics:
- Guidance on setting fundraising goals
- Best practices for acquisition campaigns and how to do them
- An overview of fundraising tools
- Advanced fundraising recommendations
- Guidance on soliciting feedback and how best to do it
Hiring staff, buying advertisements for campaigns and meeting regulatory requirements all cost money. Even parties and campaigns that rely on organic grassroots support and viral social media to elevate themselves into the public consciousness ultimately need to convert that attention into an organized, sustained campaign and funding structure to achieve their public policy goals.
For that reason, fundraising is a critical question that parties need to consider from the start. While fundraising regulations can change from country to country, and sometimes even jurisdiction to jurisdiction, it is important to have a pathway for building a campaign war chest.
In some cases, public financing may be the solution. In others, there may be a small pool of large donors willing to provide the primary source of funding. When available, your party should combine public allocations and private fundraising. Whereas a new coalition may be heavily reliant on small donations from its most fervent supports, as parties mature their pathway to electoral success may rely on some distribution of all of the above.
As you consider potential funding sources, make sure you consult campaign-finance regulations in your country and jurisdiction to understand key limitations and requirements. There are often laws governing allowable donations, requirements for financial disclosure and limits on party spending—be sure you’re familiar with these regulations before you launch a fundraising campaign, digital or otherwise.
Grassroots fundraising has emerged as a core tenet of modern campaigning, with online fundraising being a central driver of this trend. The efficiencies and economies of scale behind mass-communication tools and cloud-based resources have made grassroots fundraising more accessible and more successful than ever before. Parties should seek funding from multiple streams—from the public and from large, medium and small donors. The techniques covered below will generally be most effective when targeting small and some medium-sized donors.
Even campaigns that have other funding sources available to them can take advantage of online fundraising to illustrate grassroots support, build their volunteer networks and share their message with the broader public. However, despite all of the advantages of online fundraising, it is important to avoid assuming that the pathway to success is easy or that it will pay immediate dividends. The truth is it can take months, if not years, of building your email file and consistently emailing your audience before you can expect to see tangible financial results.
This section provides an overview of the strategies that support a successful online fundraising program, best practices to employ and an introduction to some of the technologies that support effective fundraising. As with any of the technologies that support your political party, they are meant to bolster, rather than replace, any existing efforts your party already has pertaining to fundraising.
Building A Donor List
Data Collection Opportunity
A prospective donor list is the backbone of every successful online fundraising program. In most cases, this prospective donor list is an email list that the campaign organization owns and the recipients have consented to receive. This consent could come from subscribing to this list or taking some other action on the website that qualifies as consent under the site’s terms of service
There are numerous ways for a contact to be added to the prospective donor list, including signing up on the campaign’s website, signing a form at a campaign event, responding to an online ad, via a list-sharing agreement with a likeminded organization, etc.
Regardless of how a prospective donor list grows, the important point is that once a donor is added, the marginal cost of engaging that prospective donor in the future drops significantly.
Donor Files Are Living Documents
It is useful to remember that prospective donor lists are never static. There are always new emails being added and others being removed due to users choosing to unsubscribe, changing email addresses or email bounces.
With that in mind, it is important for campaigns to put their efforts behind continuing to acquire new emails at every opportunity—such as collecting emails through the website, during events, through ads, etc.—so that the growth continues to exceed any normal attrition rates. Remember that data collection is a team responsibility and one that should be emphasized continually.
When an individual unsubscribes or you get a bounce-back email stating their email address is no longer active, make sure to remove them from the list.
Setting Fundraising Goals
While it may feel difficult to project how much an organization can expect to raise from its online fundraising efforts, one can take intuitive steps to set reasonable goals.
The following formula provides useful benchmarks for setting fundraising goals and identifying which tools to use to improve them. In cases where there is no historical data to use as a benchmark, it is recommended to use conservative placeholders until more accurate data can be compiled.
| (Number of Emails) | X | (Conversion Rate) | X | (Average Gify) | X | (Average Gifts Per Year Per Email) | = | Total Raised |
Number of emailsNumber of emails in your prospective donor list
Conversion rateThe percentage of users in your list who end up donating to your campaign
Average giftThe size of the average donation received by your campaign
Average gifts per year per emailA calculation of how many times a person gives per year
Of these four inputs, the last three are the most difficult to change. They tend to be rather static, with only marginal increases or decreases.
The number of emails is the input that campaigns have the greatest ability to significantly impact, which is why successful online fundraising programs put so much emphasis on acquiring new emails to grow the prospective donor list.
A Note on Fundraising:
Data-Collection Opportunity
Through P2P texting, you can directly contact individuals with a link that directs to a petition form or a fundraising page to have them sign up and opt in to your primary email list or SMS list. Here are some best practices.
- Utilize high-profile campaign leaders and allies as senders. Test various messages, such as the examples below, and see what gets the most engagement. Be creative with your senders.
- (Example) Subject Line: It’s official; Preview Text: Voter registration is now live! Create a sense of urgency.
- (Example) “There’s no time left to waste. Make your Election Day plan to VOTE right now and ensure you’re ready to vote TOMORROW!”
- Use a clear and early call to action.
- (Example) [PLEASE SIGN NOW >>] or [CONTRIBUTE NOW >>].
- Use web links to drive recipients back to your website.
Acquisition Campaigns and How to Do Them
Because the size of its prospective donor list is the variable over which a campaign has the most control, acquisition campaigns play a large role in online fundraising.
In its most basic form, an acquisition campaign is a deliberate strategy to grow your prospective donor email list. Unlike direct fundraising solicitations, an acquisition strategy has a lower threshold in terms of success.
Data-Collection Opportunity
Note that acquisition campaigns can serve as the ultimate data-collection opportunity for your political party.
An email list (often referred to as a housefile) is never static. There are always new emails being added and a small percentage unsubscribing. It is useful to think of this process as a natural lifecycle:
Acquisition: new emails are acquired;
Engagement: the party engages with its audience on a regular schedule; and
Response: the party learns more about its audience based on its response (open rates, link clicks, unsubscribes, etc.).
Typically, a user is willing to share their email contact because it allows them to learn more information about the campaign, participate in the sense of community or otherwise move one step closer to becoming an active donor.
Acquisition of new emails can come in many forms, including the following.
- Online advertising
- For example, Facebook has a specific ad unit for this purpose. Its lead acquisition ads are designed to autofill with the user’s data on file with Facebook, so they only need to click a confirmation without ever leaving the Facebook platform.
- Organic social media posts that direct to a web form
- Organic website sign-ups
- Event sign-ups
- Email list exchanges with likeminded organizations
It is also worth noting that acquisition campaigns do not always need to focus on capturing an email. They could also involve capturing a phone number or physical address, or growing your social media following.
Fundraising Tools
As the field of online fundraising has grown, both in terms of politics and nonprofits, organizations have the advantage of more options to choose from. These tools, which include email, text messaging and online advertising, provide a vehicle for the political party to engage online with its supporters and make its case for financial support. All of these tools only work if they include a very clear ask for a monetary donation. Be direct with your audience, give them a clear call to action and make it easy to donate.
Email Fundraising
Consistently growing your prospective donor email file is critical to building a strong digital fundraising and voter-outreach program. Prospecting and list building can be done through paid digital advertising, peer-to-peer texting, renting or buying lists from likeminded organizations, and organically through your website or social media.
Tips for building your prospective donor email file:
- Start early. It takes time to acquire and build an effective email list. In some cases, it may take six months to a year to see the full return on investment.
- Keep your audience engaged. Make sure to send to your audience consistently but without overwhelming them. As you send, try new and engaging content to add variety and to keep everyone engaged.
- In addition to “hard asks” for donations, mix in opportunities for feedback and engagement, including petitions, surveys and other opportunities to become involved in the party movement.
- Make it personal. Many email service providers include a merge tag, which allows the recipient’s name to be merged into the copy in place of a variable. Further information on how to do this can be found on your email service provider’s FAQ resource page.
- Give a clear call to action. This helps your audience know exactly what you expect from it and increases the likelihood of the audience following through. Be direct and unambiguous.
How do you know if you are sending too many emails? Keep an eye on your unsubscribe rate, which can be found on the email service provider’s dashboard. An unsubscribe rate below 5 percent may be typical, but could be a sign of concern if it grows above that mark. Stay aware of what unsubscribe rate is typical for your organization and watch out for significant increases.
Digital ads are often the largest source of new emails for a campaign or state party because they allow you to reach a large portion of the electorate at a modest price point. Because of their scale and the ability to match the ad with the user’s interest, Facebook and Google Search are the best digital ad platforms for initial prospecting.
A good guideline for digital fundraising is to try to achieve a 1:1 ratio with the amount invested in growing your list— meaning aim for a dollar raised for every dollar spent on digital ads. By achieving this ratio, a political party can hope to sustain its fundraising program without losing a significant amount of money. The objective is to move your engagement with the prospective new member or voter from an online ad, which is a relatively expensive mode of communication, to email, which is considerably cheaper on a per-contact basis.
It is important not to become alarmed if an online advertising prospecting plan does not generate high returns immediately. The goal is to grow the size of the party’s email list, knowing that most donations will occur as Election Day grows nearer and more prospective donors become aware of the stakes. Investing early in growing your email file creates more opportunities for donors to give and thereby increases the lifetime value of your email list.
Text Messaging
As the email-solicitation industry has exploded, the competition for email inboxes has become more intense. Seeking an additional entry point, many political parties have begun to incorporate text messaging, or SMS, into their marketing mix.
SMS has the benefit of bypassing apps and going directly to notifications on the mobile phone. It has a record of higher engagement rates and, unlike P2P messaging, can be used to message entire lists of people at one time.
Tips for building your prospective donor SMS list:
- Start early. It takes time to acquire the phone numbers of users who have opted in to receive texts from your organization. In some cases, depending on local campaign-finance regulations, acquisition can begin during the preparation phase, before a campaign has officially launched. It is popularly said, “The best time to begin acquiring new prospects was yesterday.”
- Make sure to consult with your legal team to ensure you are following all legal guidelines on opt-in language as you begin building your SMS list. Opt-out language (such as including “Stop2end” at the end of a text) and your links must include proper disclaimer language.
- Test your message. Sending messages costs money, and resources are limited. Send test messages to a smaller, randomly selected subsection of your audience to see what performs best. Once you have a winner, send it to the rest of your list.
- Keep your audience engaged. Make sure to send to your audience consistently, without overwhelming them. As you send, try new and engaging content to add variety and maintain engagement.
- Track your conversions and costs using Urchin Tracking Module (UTM) tagging on all of your links. UTM tags, or tracking tags, are the extended links one will often see when clicking on a link from a marketing email or from social media.
Example of UTM tagging on a (link):
https://www.example.com/page?utm_content=buffercf3b2&utm_medium=social&utm_source=snapchat.com&utm_campign=buffer
These tags help distinguish traffic coming from distinct campaigns. This system allows you to identify which campaigns are most successful
See this guide for a more in-depth discussion of UTM tags.[43]
Build your own UTM campaign tags here.[44]
- Create opt-in keywords for specific goals and occasions. These distinct keywords will allow you to distinguish unique campaigns and compare their results (e.g., Text VOTE to 80810).
- Have a conversation. Don’t always send a message that sounds like you’re talking at the recipient. Experiment with informal messages to seem more personable and conversational.
- Don’t overdo it. It’s important to gauge the health of your list and not send too frequently. (As with email, your unsubscribe rate is a helpful tool here. While some unsubscribes are typical, any significant shift could mean a change in cadence is warranted.)
- Follow up (again). Sending follow-up messages is an effective way to reengage with people who may not have read or even opened your previous message. If you see a particular message working well with other people in your audience, try sending it with slightly updated copy to non-responders.
- Plan ahead. Knowing important dates in advance can help you plan your sends. Put together a calendar and schedule your messages no more than a couple of days in advance. (This content calendar can be built in consideration of all of your communications channels including email, social media, press releases, press conferences, etc.).
- Be concise.
[43] Mineo, Ginny. “UTM Codes: How to Create UTM Tracking URLs on Google Analytics.” Hubspot, Sept. 2013, blog.hubspot.com/marketing/what-are-utm-tracking-codes-ht#:~:text=UTM%20(Urchin%20Tracking%20Module)%20codes,a%20link%20to%20this%20URL.
[44] “URL Builders.” Google. Accessed 17 Aug. 2022, support.google.com/analytics/answer/1033867?hl=en.
Advertising
Voters increasingly get their information from the internet. This can be from online news publications, social media networks or email newsletters. The funding model for these media channels is often built on selling advertisements, which creates an opportunity for campaigns to buy ads and leverage these platforms to reach potential supporters.
In terms of strategy, paid digital advertising is the entry point to a longer-term conversation with potential supporters. It provides the opportunity for a campaign to make potential supporters aware of the campaign and its platform. The goal is to walk away from the encounter with the audience interested in learning more and potentially becoming involved with the cause.
Advanced Recommendations: Building an Online Fundraising Technology Stack
If your political party has available resources to build upon some of the more accessible and low-cost tools discussed above, consider investing in an online technology stack—essentially a combination of tools used to provide or enable a complex digital fundraising effort—to integrate advanced tools to conduct more efficient and effective outreach. Investing in an email service provider, a CRM and a well-established and designed donation page can help to increase the efficiency of your fundraising efforts, if your resources allow. Each of these tools requires additional funds and technical know-how compared to the more accessible tools listed above, but can yield much greater fundraising results if synchronized.
Email Service Provider
Your ESP will help to provide insights on how to reach your goals as you begin email marketing campaigns. A good ESP (see examples below) can amplify your traditional email outreach by providing analytics on deliverability, open rate and click-through rate for each of your messages. It can also be useful if your donor list has grown to more than a few hundred people, as it can expand the number of individual emails to which you can reach out at a given time. You can utilize these metrics to refine your messaging plan and tactics in later stages.
- Considerations for choosing an ESP
- Cost: What is the cost per email?Integrations: Does it integrate with CRM data management?
- Deliverability: Does it enable you to manage deliverability issues?
- Security: What security features does it offer?
Your ESP will help to provide insights on how to reach your goals as you begin email marketing campaigns. A good ESP (see examples below) can amplify your traditional email outreach by providing analytics on deliverability, open rate and click-through rate for each of your messages. It can also be useful if your donor list has grown to more than a few hundred people, as it can expand the number of individual emails to which you can reach out at a given time. You can utilize these metrics to refine your messaging plan and tactics in later stages.
- Considerations for choosing an ESP
- Cost: What is the cost per email?Integrations: Does it integrate with CRM data management?
- Deliverability: Does it enable you to manage deliverability issues?
- Security: What security features does it offer?
Customer Relationship Management
When you set up your ESP, ensure any form sign-ups you receive—whether through social media posts, your website or other media—seamlessly enter into your email list maintained in your ESP. This ensures you don’t miss any potential opportunity to raise money from the new emails you have acquired. Your CRM should have the ability to integrate with multiple ESPs and should have user-friendly functions that do not require sophisticated users.
Donation Page
Finally, a secure web form capable of processing online donations made with a credit card will be critical to your online fundraising efforts. It is paramount that your supporters have faith that their donations will be processed securely. To that end, you should look for platforms that are able to process donations in local currency and have a strong reputation for security. While the best service may vary from country to county, it is often useful to see what other nonprofit organizations are using in your locality. If possible, integrate or link this donation page within your broader party website.
- Pay close attention to the fee structure and find the best balance of ease of use with the lowest fee per donation.
- Look for donation-management platforms that allow you to track the effectiveness of an online marketing campaign across traffic sources and publishing media (i.e., UTM campaigns) or to compare specific campaigns.
- Many donation platforms will allow you to create multiple landing pages that can contain different imagery and messaging.
- The form for completing a donation should be clean and efficient without unnecessary fields, and should be easy to complete for both desktop and mobile users.
When building your own technology stack, the objective is to identify different tools for each part of the user journey that work well together. The ideal scenario is to be able to pass data from one tool to another in order to draw insights on how effectively the program is working as a whole.
For example, the email service provider breaks down each user according to their unique email address. This email address should connect with a specific email address within your CRM and the email address associated with a contribution on your donation page. Integrating this data on a macro level allows your organization to better understand your online fundraising information and identify where users may drop off, and thereby look for opportunities to improve.
Importance of Soliciting Feedback (And How to Do It)
Communication with supporters and potential supporters should not be a one-way channel. Your party should create the opportunity for supporters to share their input, feedback, goals and priorities with the party. Regularly soliciting input is key to projecting responsiveness and connection to potential supporters, and can help your party better understand what constituents care most about. Soliciting feedback is critical to informing your party priorities, goals and messaging, and will help your party remain relevant and aligned with the interests of voters. Crowdsourcing and polling are two methods to solicit input and are explained below.
Data-Collection and Data-Application Opportunity
Online polling and crowdsourcing can enable you to collect contact, interest and other information about your voters, as well as serve as an opportunity to use existing data to conduct outreach in a targeted and informed way. Refer to your contact database to segment voters along demographic, location and issue area lines to inform who you should contact and in what ways.
Crowdsourcing and How to Do It
Often the most effective way to identify which issues are of importance to your supporters, and around which priorities you should be centering your platform, is to simply ask them. Digital platforms have made receiving feedback easier than ever before. Below are a few simple solutions for gathering feedback from your supporters and providing them with a sense of ownership over the process.
- Open-ended questions on social media platforms, such as Facebook, Twitter and Instagram: Social media are exactly that—social! Old forms of media, such as television and radio, were one-way conversations. Social media offer the opportunity to converse and recognize more voices. Ask people what they think using open-ended questions across the party’s social media platform; they will tell you.
- Crowdsourcing content: Personal stories can often provide the most persuasive arguments. Asking your supporters to share their stories, pictures or videos can help the political party paint a more vivid illustration of the change you seek to achieve and why.
- Web forms and website surveys: Sometimes the responses that you seek may be more sensitive. Or, rather than individual anecdotes, you may be seeking to identify points of consensus around key priorities and issues of concern. In these cases, creating a web form or survey to collect input may be the best route to help inform your party’s core focus.
Key Tip: Google Surveys offers a free and easy solution for creating surveys, in case the party website does not have this feature available.[45]
- Online petitions: These are simple and powerful tools that allow you to build your database and define what points allow for mobilization of your base—which can, in turn, be translated into action (vote, donate, etc.), immediately or later. These should focus on a single issue and help you refine your database for stronger future use.
[45] Google Surveys. Accessed 17 Aug. 2022, surveys.google.com/warm-welcome?dest=%2Fyour-surveys.
Online Polling and When to Use It
Similar to crowdsourcing strategies, online polling can be a useful method for gathering useful feedback. Not only can online polls be informative, but they can also serve as engaging content on social media to keep your audience members engaged.
Facebook, Twitter and Instagram have easy-to-use polling features.[46] These tools can be useful for gathering responses as well as reinforcing to supporters that their voice matters. It should be noted, however, that opt-in surveys and polls are not scientific and are subject to participation bias meaning the results are not necessarily representative of the community as a whole.
In cases where a more rigorous methodology is needed, online polling services such as Pollfish can provide value as a cost-effective alternative to hiring an organization to conduct campaign survey research and focus groups—otherwise known as a pollster. The Pollfish platform is easy to use and can help parties build more representative models of interests and priorities across their constituencies, as opposed to informal polls launched through social media. (The availability of Pollfish or other alternatives may vary from country to county.)
[46] “How Do I Created or Edit a Poll in a Facebook Group.” Facebook. Accessed 17 Aug. 2022, facebook.com/help/175694272486085; “About Twitter Polls.” Twitter. Accessed 17 Aug. 2022, help.twitter.com/en/using-twitter/twitter-polls; Demarest, Abigail Abesamis. “How to Make an Instagram Poll to Ask Questions or Survey Your Followers.” Instagram, 31 Aug. 2021, businessinsider.com/instagram-polls.
Annexes
Annex A. Guiding Checklist: A Resource to navigate the political parties playbook
This checklist is written as a step-by-step guide to accompany any party or individual reading the Political Parties Playbook. It is intended to provide actionable guidance and key steps a political party should take to put the toolkit’s recommendations and best practices into action. The checklist has been structured to mirror the primary sections of the toolkit and the key lessons within each. Feel free to refer to the checklist sections most relevant to the party’s core needs.
Getting Started
- Check local, national and regional level regulations around data use.
- Check local, national and regional campaigning and finance laws, as well as any other laws that cover political party activity.
- Before integrating any new tools, establish cybersecurity as a priority for your political party at both the individual and party level. Ensure staff and volunteers use two factor authentication, understand how to circumvent phishing attempts, and carefully manage access to sensitive information, among other cybersecurity best practices listed in Annex B.
Internal Communications
- Step one requires understanding the party structure needed to make your digitization efforts a success. Review the party roles flow chart. Decide who will be responsible for each aspect of party management, including new digital elements, and ensure they understand their role within the party ecosystem.
- Does your party have an IT team? If not, consider hiring or contracting an IT team or an IT administrator who can serve as the technology expert and assist staff with questions or troubleshoot problems. If you do not currently have sufficient funds for IT support.
- Evaluate what digital tools your party currently uses for internal communication and collaborate with party colleagues to identify gaps and needs. Your party should not use digital tools just for the sake of doing so, but should instead figure out how and which digital tools can improve your internal communications. A few of the types of tools to consider are:
- Messaging Platforms
- Project Management
- Video Conferencing and Audio Conference Calls
- Cloud Suites
- Digital File Sharing
- Identify which of the above types of tools your party would like to integrate and in what order of prioritization, and then make a plan for setting these tools up and introducing them to your staff.
Contact Management
- Establish a strong understanding of what data is, why it’s valuable to your party operations and what information you would need to collect on contacts and voters.
- Foster a data-driven culture within your party. Ensure that every member of the party understands the importance of data and that they have the responsibility to collect data at every opportunity.
- If not already established, determine how you would like to structure an individual record, including what system of unique identifiers you’d like to use. For more information on individual records.
- Create tags for the fields that are most important to your party. For more information on tags.
- Remember to avoid a “catch all” notes column in your individual records which can make your database unmanageable. Build a practice of self-discipline across your party to create a new category, or tag, for each new data point so your databases remain manageable and useful into the future.
- Keep your data organized.
- Work towards building and systematically maintaining a database, either through a spreadsheet or a more elaborate Customer Relationship Management (CRM) software, that includes each of the individual records.
- Make data digital in the first place, where possible. Instead of spending hours transferring data from a physical sign-in sheet, use a short digital sign in form that automatically populates the results into a database. If your data isn’t already digitized.
- Ensure that your data is stored in a commonly recognized format (.csv or .xls for example) so that you have the ability to easily export the data or transfer the data from one platform to another.
- Note that some countries, including those in the European Union, have requirements around the “right to data portability,” so check your local regulations to see if your country has similar requirements.
- Review the principles for creating a strong database environment. Ensure that whichever database you have chosen prioritizes data access, data integrity and data security.
- As your lists of data grow and become more difficult to manage, consider the differences between spreadsheets and CRMs and potential advantages of paying for a CRM to help manage your data
External Communications
- Revisit (or establish) the key values your party wants to be core to all external communications. Frequently revisit these values to be sure they’re consistently expressed throughout your messaging.
- Remember key values should not be decided by the party in isolation, and should be driven by citizen concerns. See guidance on soliciting priorities and key values from citizens to help inform the values of your party.
- Establish a well-structured communications team to manage your different communication goals and tools, or at minimum clearly assign roles and responsibilities related to external communications if you do not have the resources to build a full team.
- Take the time to train your external communications team on the key components of effective digital communications, including how to build trust, how to manage crisis communications and how to combat mis/disinformation.
- Develop a social media strategy to guide your use of digital tools, including how you plan to integrate those digital tools into existing analogue communication strategies.
- As you develop a social media strategy, think through opportunities to collect contact information from potential new members as a way to grow your contact list and expand your messaging reach. Consider the ladder of communications and how you can integrate that principle into your work.
- Does your party have a central platform to clearly communicate your party values in a centralized place, such as a website or Facebook page?
- If you don’t have a central website, see guidance on creating a party website as a critical resource to share your party’s core values and goals.
- Take the time to convene across the party to take stock of the digital tools your party is already using to communicate externally with members or potential members.
- Review existing digital tools that could be easily integrated into your communications, taking special consideration of where/how your target audience is already online and accessing information.
- Consider augmenting your use of digital platforms and other communication tools by integrating digital advertising into your external communications strategy.
- Establish metrics to track engagement with your party’s messaging, including establishing Key Performance Indicators (KPIs) to evaluate the success and reach of messages and determine which digital tools are reaching the most number of people.
- Iterate, test, and adapt your external communications approaches, including the types of messages and tools you use, to continue to seek to improve your party’s reach.
- If not already in existence, establish a digital database to manage contacts and ensure your communications are reaching the appropriate audiences. See guidance on campaigning and the role databases can play.
Fundraising
- As you consider potential funding sources, be sure to research and understand all local and national requirements and regulations on fundraising that you must follow.
- Build a prospective donor list
- Refer to the Ladder of Engagement as you vary your fundraising approaches.
- Keep in mind that donor lists are never static with new emails being added and others being removed due to users unsubscribing, changing email addresses, or inactive email accounts.
- Continuously acquire new emails at every opportunity – through your website, during events, through ads, etc.
- Remove individuals from your donor list if they unsubscribe or if their email is no longer active.
- Mix requests for donations with opportunities for feedback and engagement, including petitions, surveys, and other opportunities for involvement.
- Give a clear call-to-action.
- Set fundraising goals and identify which tools to use to improve those goals.
- Determine which tools your party will use for fundraising. A few tools to consider are:
- Text messaging
- Advertisements
- Consider buying ads and leverage online news publications, social media networks, or email networks to reach potential supporters
- Consider conducting an acquisition campaign to grow your donor list
- Keep in mind acquisition campaigns do not need to solely focus on email. It could also involve capturing a phone number, physical address, or growing your social media following
- Consider investing in creating an online technology stack to integrate advanced tools to conduct more efficient and effective outreach.
- Ensure online fundraising efforts utilize secure platforms for acquiring donations.
Annexes (Guiding Checklist Continued)
Annex B: Cybersecurity
- Create a cybersecurity plan for your organization that addresses security at the individual level and the party level.
- Create unique passwords, do not share them, and update them regularly.
- Enable Two Factor Authentication on all accounts.
- Keep all software up to date.
- Understand and be vigilant towards phishing attempts.
- Restrict account access to only those who need it.
- Secure physical offices and devices.
- Keep information on cybersecurity and digital safety resources handy so that you can access it easily in emergency situations.
- Consider the need for a VPN and distribute them to staff when necessary.
Annex C: Access and Inclusion Online
- Think critically about the platforms, tools, and technologies you will use to conduct party business and outreach, consider who will and won’t be reached through those platforms and tools.
- Consider how to include vulnerable groups virtually, as well as any special considerations they may require.
- Make sure your content is smartphone friendly since the majority of people consume content online via phones.
- Consider cost barriers, such as the cost of accessing data or other costs associated with connecting to the internet. Consider supplementing live streaming with messages on radio or TV to reach those who cannot overcome the cost associated with internet use.
- Meet your audience where they already are. You will not easily get your constituents to visit a new platform or use a new type of technology. Think about what social media platforms and information sources your audience already uses, and then conduct operations on those platforms.
- Create a plan for reaching constituents who are unlikely to receive your message through digital platforms. For more information on doing this efficiently.
Annex D: Legal Regulations
- Remember you are responsible for ensuring your party follows all local and national regulations. Local and national regulations supersede all advice in this playbook.
- Research and understand all regulations governing political party operations.
- Research and understand all financial regulations.
- Research and understand all regulations around data.
- Research and understand all campaign and election regulations.
Annex B. Cybersecurity
Cybersecurity, the art of protecting networks, devices and data from unauthorized access or criminal use—and the practice of ensuring confidentiality, integrity and availability of information—is a critical aspect of operating a political party, especially as more operations occur online. You should consider security from both an individual and organizational level guided by the best practices below.
Individual-Level Security
- Security is the responsibility of each individual associated with your party. Investing in trainings, so that everyone understands the role they play in your party’s security, can be an important tool for saving time and resources in the long term. A few basic security practices for all individuals to keep in mind include the following.
- Do not share your password, especially over the phone or over email, even if the person asking for your password claims to be tech support.
- Enable two-factor authentication on all accounts. Take a look at this guide for more information.[47]
- Use a password that contains letters, numbers and special characters. Do not use basic passwords such as “password” or your party name.
- Change passwords regularly, such as every three months.
- Use a reputable password manager, such as Bitwarden (free and paid options), LastPass or 1Password, among others.
- Do not allow unauthorized individuals to access your computer, mobile phone or other software or devices at any time.
- Keep all software up to date by regularly checking for updates for your operating system and third-party apps.[48]
- Beware of phishing attempts. Phishing is when attackers send emails that try to steal data or personal information. Do not click on any links or open any attachments unless you know they are safe. Take a look at this guide for more information.[49]
- Log out of accounts when not actively using them.
- Protect individuals, particularly women and other minority staff and candidates, from harassment online. Many marginalized groups are targets of harassment and will need additional security and protection. Take a look at this guide for more information.[50]
[47] Garun, Natt and Barbara Krasnoff. “How to Set Up Two-Factor Authentication on Your Online Accounts.” The Verge, 10 June 2021, theverge.com/22215571/factor-authentication-2fa-apple-microsoft-google-how-to.
[48] “How to Update Your Software.” GCFGlobal. Accessed 17 Aug. 2022, edu.gcfglobal.org/en/basic-computer-skills/how-to-update-your-software/1/.
[49] “A Short Guide for Spotting Phishing Attempts.” Center for Internet Security. Accessed 17 Aug. 2022, cisecurity.org/insights/blog/a-short-guide-for-spotting-phishing-attempts.
[50] “Online Harassment Field Manual.” Pen America. Accessed 17 Aug. 2022, onlineharassmentfieldmanual.pen.org.
Party-Level Security
- Party-wide security operations must also be considered. IT staff should be included in managing all party-level security. This responsibility should not reside with a candidate or campaign manager, but with someone such as the IT administrator, who is equipped to prioritize security and assist with any technical challenges. A few best practices to keep in mind across party operations follow.
- Anyone working for the party (staff, members, consultants, contractors, etc.) should only have access to the computers, software and files necessary for their roles. Additionally, each individual should have unique logins and accounts. When possible, stay away from multiuser or group username/password combinations.
- Do not publicly disclose your party’s security practices.
- When an employee or volunteer leaves the party, ensure that their user account is deleted and any shared accounts to which they had access are reset with new passwords.
- If sharing an account on social media, make sure to change the password on at least a monthly basis. As noted above, change it off cycle when an employee or vendor who used to have access to the account leaves.
- Screen new employees and vendors carefully to ensure they do not have a history that could harm the party’s reputation or security, or potentially become an insider threat.
- Secure physical offices and devices from surveillance and theft.
- Train staff on best security practices regularly (provide refreshers), including safe storage and management of party-owned devices with sensitive information. A stolen laptop could give the thief access to sensitive data.
- Maintain physical security of the workplace. Lock the doors and only give access to trusted individuals.
- Implement an organization-wide requirement to change passwords regularly, typically every three months.
- Back up data regularly to a secure platform.
- Protect the party’s website using a cyberattack-mitigation platform such as Cloudflare or Deflect.
- Use VPNs to protect your party’s internet traffic from intruders (see pop-out box for additional guidance). This can be especially important if staff are using party computers or mobile phones on public wifi or untrustworthy networks.
Cybersecurity and Digital Safety Resources
- The Rapid Response Network and CiviCERT created a Digital First Aid Kit that is a great resource for emergency situations, such as when you lose access to your social media account, your website is attacked or you are facing harassment online.[51]
- Security in-a-box: Collection of digital security tools and tactics[52]
- Security First’s Umbrella App gives you free digital and physical security advice.[53] Security First also has online training courses (in English) on various topics, including secure communications and phishing-attack defense.[54]
- Access Now’s Internet Shutdown and Elections Handbook[55]
- Access Now’s “A First Look at Digital Security”[56]
- Access Now’s Digital Security Tips[57]
- The Cybersecurity Campaign Playbook includes guidance on safely conducting a digital campaign.[58]
Consider requiring staff to use a VPN
- Use encrypted forms of communication as encryption scrambles the data, reducing the likelihood that someone can read your messages even if they intercept the data. Signal and Virtu Email are good places to start.
- Protect your party’s website from cyberattacks. Look into a website attack-mitigation platform, such as Cloudflare or Deflect.
- Consider requiring staff to use a VPN.
VPNs
VPNs can play an important role in circumventing censorship and avoiding surveillance. They allow you to access the internet through the VPN’s own servers instead of through your ISP. ISPs, particularly at the state’s request, can monitor, disrupt or tamper with your internet traffic.
- When looking at specific VPNs to use, consider the following.
- Choose a VPN provider that does not collect any information on its users or its users’ activity on the web by default. Assume that a VPN will collect and share your data unless you know otherwise. This way, when a government requests data on VPN users, the VPN provider does not have any data to share.
- Choose a VPN that regularly publishes (not just conducts) third-party security audits and transparency reports.
- Download a VPN before you need it. If you have an election coming up and are worried about access, or believe your party or individual staff at your party could be the target of surveillance, download a VPN now so it is ready to go when you need to use it.
- It is less suspicious to always use a VPN than to only use a VPN to visit certain websites. If you use a VPN, use it every time you access the internet.
- Do not use a free, unsecure VPN. Although VPN prices are sometimes high, this should be a priority for funds if your party operates in a repressive context.
- For more information on determining a secure VPN option, refer to this VPN white paper.[59]
[51] “Digital First Aid Kit.” Rapid Response Network and CiviCERT. Accessed 17 Aug. 2022, digitalfirstaid.org/en/index.html.
[52] Security In-a-Box. Accessed 17 Aug. 2022, securityinabox.org/en.
[53] “Umbrella.” Security First. Accessed 17 Aug. 2022, secfirst.org.
[54] “Services and Training.” Security First. Accessed 17 Aug. 2022, secfirst.org/training/.
[55] “Internet Shutdowns and Election Handbook.” Access Now. Accessed 17 Aug. 2022, accessnow.org/internet-shutdowns-and-elections-handbook/.
[56] “A First Look at Digital Security.” Access Now, Oct. 2020, accessnow.org/cms/assets/uploads/2020/10/A-first-look-at-digital-security-OCT2020.pdf.
[57] “Protect Yourself and Your Community: Use These Digital Security Tips.” Access Now, 6 Dec. 2018, accessnow.org/protect-yourself-and-your-community-use-these-digital-security-tips.
[58] “Cybersecurity Handbook for Political Parties.” National Democratic Institute for International Affairs, 2023, https://parties.cyberhandbook.org/.
[59] Grauer, Yael. “Security and Privacy of VPNs Running on Windows 10.” Consumer Reports, 2021, digital-lab-wp.consumerreports.org/wp-content/uploads/2021/12/VPN-White-Paper.pdf.
Annex C. Access and Inclusion Online
Don’t forget to think critically about the platforms, tools and technologies you will use to conduct outreach and communicate, with a keen eye toward inclusivity. Online programming can exclude the participation of vulnerable, and often significant, demographics. Consider how to include vulnerable demographics in your digital-communication plan by choosing platforms that are free or widely accessible, communicating at times of the day that allow women or youth to join, and directly reaching out to those who may need more targeted contact, such as the elderly.
Given the breadth of socio-economic variables that affect digital access and inclusion, there is no one-size-fits-all digital-outreach strategy. Diversifying your communication platforms will help you reach larger portions of the population and will ensure you are reaching your audience in a democratic and inclusive way. Large-scale automated calling (i.e., robocalls) can be used to reach those without internet; call-in hotlines using an interactive voice response system can share prerecorded information and facilitate routing callers to the most appropriate assistance; WhatsApp messages can target mobile phone users; and live press conferences reach those with access to streaming services.
A few questions to consider include:
Who has access to the internet? Who doesn’t?
The “who” should take into account economic inequality; urban versus rural; ethnicity; religion; tribal internet access and habits; gender; age; and any other notable indicators that impact internet access in the community you are trying to reach. If there are groups that have no access, consider augmenting digital outreach with targeted communications to those groups using accessible tools such as phone calls and SMS messages, and—if appropriate for your context—including a call to action for word-of-mouth campaigns in digital communications.
How fast is the internet access of those you want to reach? Are there inequities in internet speeds?
In general, live video with multiple participants requires high-speed internet; live video from a single person requires moderately high-speed internet; recorded videos can be more easily played back in low-speed environments, but still require a reasonable internet connection; small infographics and pictures will work for most; and text posts need limited connections. Direct messages over platforms such as WhatsApp, Telegram or Signal require very little bandwidth. For example, if you are trying to reach low-income groups in rural areas whose internet speeds are slow, a live video conference will be ineffective.
How do your constituents access the internet?
As a general rule, make sure your content is smartphone friendly, as that is how most people consume content online. Most major platforms today are built for mobile access, but government and party websites often aren’t. This is easy to fix. If you post a video or piece of information on your official website, be sure to post it across other platforms as well. To reach those with older phones, be sure to communicate critical information through simple SMS messages as well.
Also consider privacy and safety. If the information you are sharing is sensitive, or if it would indicate something personal about the person reading it, consider the implications of that information being consumed on a shared device or in a public setting.
Finally, consider cost barriers for your members and message recipients. While an individual or household may have access to the internet, the cost of data or other costs associated with connecting to the internet may prohibit some from engaging. Consider supplementing live streaming of events with messages broadcast on the radio or TV to reach those facing cost barriers for internet use.
What social media platforms and information sources do your constituents already use?
Different demographic groups use different social media platforms. This is not consistent across contexts and, as such, there is no one-size-fits-all approach. However, in general, Twitter is often used by elites and journalists, making it an excellent communication mechanism if you are looking to have your message amplified by the press. Facebook is popular across demographic groups and some carriers allow its access without incurring any data charges. TikTok and Instagram tend to be used by younger demographics. Content style and distribution should be tailored to the audience you are trying to reach (see page 41 for guidance on use of social media platforms in your external communications outreach).
For those who are unlikely to receive your message directly through online messaging, consider the following:
- Include a request for word-of-mouth sharing in your digital communications. For example, if only young people are likely to see your Instagram post but they live in an intergenerational household, a call to action that encourages them to share the information with their families may be effective.
- Target outreach to specific communities or demographics. This should be responsive to the communications habits and trust structures of your target audience. If you have been able to reach the vast majority of your target audience online, but have not been able to reach the elderly, consider what communications channels they use and create a campaign specifically for them. You may augment your digital outreach with radio interviews/announcements, or sending physical letters—or by working with other community leaders who are accustomed to communicating with those groups. Digital outreach is not effective when it doesn’t reach the audience you want to reach.
- Not all individuals have access to, or are proficient in, the technology used for digital communications; thus, political parties may need to supplement the technological solutions and strategies presented throughout the playbook with ones that are more analog. For example, remember that some individuals may rely on landlines rather than cell phones (not smartphones), or newsletters rather than email. Augment rather than fully replace analog communications.
Using digital communication to increase accessibility
Digital communication allows for the rapid creation and distribution of content in multiple different formats, which can help your party reach more people, including those who have historically been left out. Make sure your content can be consumed in a number of different ways. For instance, if you create a video message or are conducting a video conference, turn on automatic subtitles or use a platform that includes that feature as an option to ensure that those who are hard of hearing or who otherwise cannot listen to sound (shared household, sensitive content, etc.) can read the text. If you create a text-based piece of content, ensure it is machine readable, so that those who are blind or illiterate can listen.
For more information, the 18f Accessibility Guide includes in-depth tips and resources for ensuring online engagement is as inclusive as possible.[60]
[60] “Accessibility Guide.” 18F. Accessed 17 Aug. 2022, accessibility.18f.gov.
Annex D. Considering Legal Regulations
Legal regulations governing political parties and their various activities will vary by country—and at times, even by city or jurisdiction. As such, this playbook does not intend to provide direct guidance on how to comply with regulations. Instead, we would like to highlight a few specific questions your party should consider and investigate to better understand the regulations that will specifically apply to the party’s activities in its unique operating context. It is your responsibility to understand and comply with all regulations governing political parties in your municipality, state, country or otherwise. No advice in this playbook supersedes legal requirements.
Typically, regulations will govern general political party activities (beyond electoral activities), campaign finance and the abuse of state resources for political gain. International obligations for elections are outlined in this resource [61]. We’ve included a few guiding questions your party should consider in the context of finance and data regulations which are frequently sensitive and highly regulated activities. Campaign finance is defined as “financial transactions to political parties or candidates related to an electoral campaign, which could include formal, financial or in-kind donations of expenditure.”[62] Keep in mind that there can be different rules for online and offline activity, and your party needs to understand both sets of legal regulations.
Data Regulations:
- What, if any, data-protection laws exist? Have you identified all relevant laws and reviewed them (both country and regional)?
- What types of data are regulated? What is considered personal data?
- Are you collecting that data? If so, are you complying with laws regulating its use?
- Are you following guidelines regarding the sharing of data across systems?
- Is your party’s data collection in line with regulations?
- Are there regulations governing data management and storage?
Additionally, consider existing campaign and election laws and regulations that might govern your political party’s activities on these topics. These should be found in the guidelines published by your local and national governments.